Biometrics in banking are moving from innovation labs to the front door of every app. The banking sector faces rising digital transactions, more devices, and customers who want instant access without giving up privacy. Financial institutions must prevent fraud at scale while keeping journeys simple. This article explains how biometric authentication and biometric verification methods work in real banking services, why they’re increasingly important for authentication and security purposes, and how to ensure compliance with modern standards.
It’s possible to deploy biometrics in FinTech that are both safe and seamless. Properly designed biometric systems deliver enhanced security and better UX simultaneously. They’re now a crucial safety feature and a signal that banks are responding to social trends, helping customers trust digital banking more.
Trust drives adoption in financial services—and fraud keeps testing that trust. Customers expect instant, private access across mobile devices, desktop PCs, and connected watches, while risk and compliance teams need strong, audit‑ready controls. Passkeys paired with biometrics—reduce phishing risk and remove friction across mobile apps and the web. See supporting evidence in the ECB & EBA SCA report and FIDO 2025 resources.
What we mean by biometrics in banking: Using unique physical characteristics—facial features, fingerprints, iris scan/iris recognition, and voice recognition—to confirm a person’s identity and a customer’s identity. In modern designs, biometric data is matched on the device by a biometric sensor (e.g., fingerprint sensors or facial recognition technology) and unlocks a device‑bound private key for authentication. This approach securely stores the reference template and reduces the chances of attackers gaining unauthorized access.
"From an engineering perspective, it’s worth remembering that all biometric use cases in banking ultimately build on two fundamental primitives exposed by device platforms: verifying that the user is physically present, and confirming that the same user who enrolled biometrics is now unlocking cryptographic material protected by those biometrics. Everything else—whether it’s passkeys, frictionless sign-ins, payment approvals, or step-up authentication flows—layers on top of these building blocks. For developers, this means that the reliability of banking journeys depends not only on biometric sensors themselves, but also on how securely and thoughtfully we design the flows that consume these primitives."
Marcin Michałek, Senior Android Developer at Miquido
Why banks are betting on biometrics
The password era is ending because it asks customers to carry a risk they can’t control. Digital banking has exploded; people hop between online banking, mobile banking, and card payments with Apple Pay and Google Pay. At the same time, attackers automate credential stuffing and social engineering. Unlike passwords, passkeys plus biometric security turn the phone or laptop into the authenticator, making phishing much harder (Digital Identity Guidelines).
Passwords are brittle; credential theft remains a dominant breach driver. Customers now expect fast, private sign‑ins across devices. Passkeys paired with biometry reduce phishing risk and speed journeys because there’s no reusable password to steal. In practice, biometric technology checks a reference template on‑device and releases a private key—so there’s nothing useful for an attacker to phish.
Omnichannel reality: In one day, a customer checks balances on a mobile phone, approves a notification on connected watches, taps to pay with Apple Pay or Google Pay, and finishes an application on desktop PCs. Biometric authentication follows them across mobile apps and the web, so sign‑in and approvals feel natural wherever they engage.
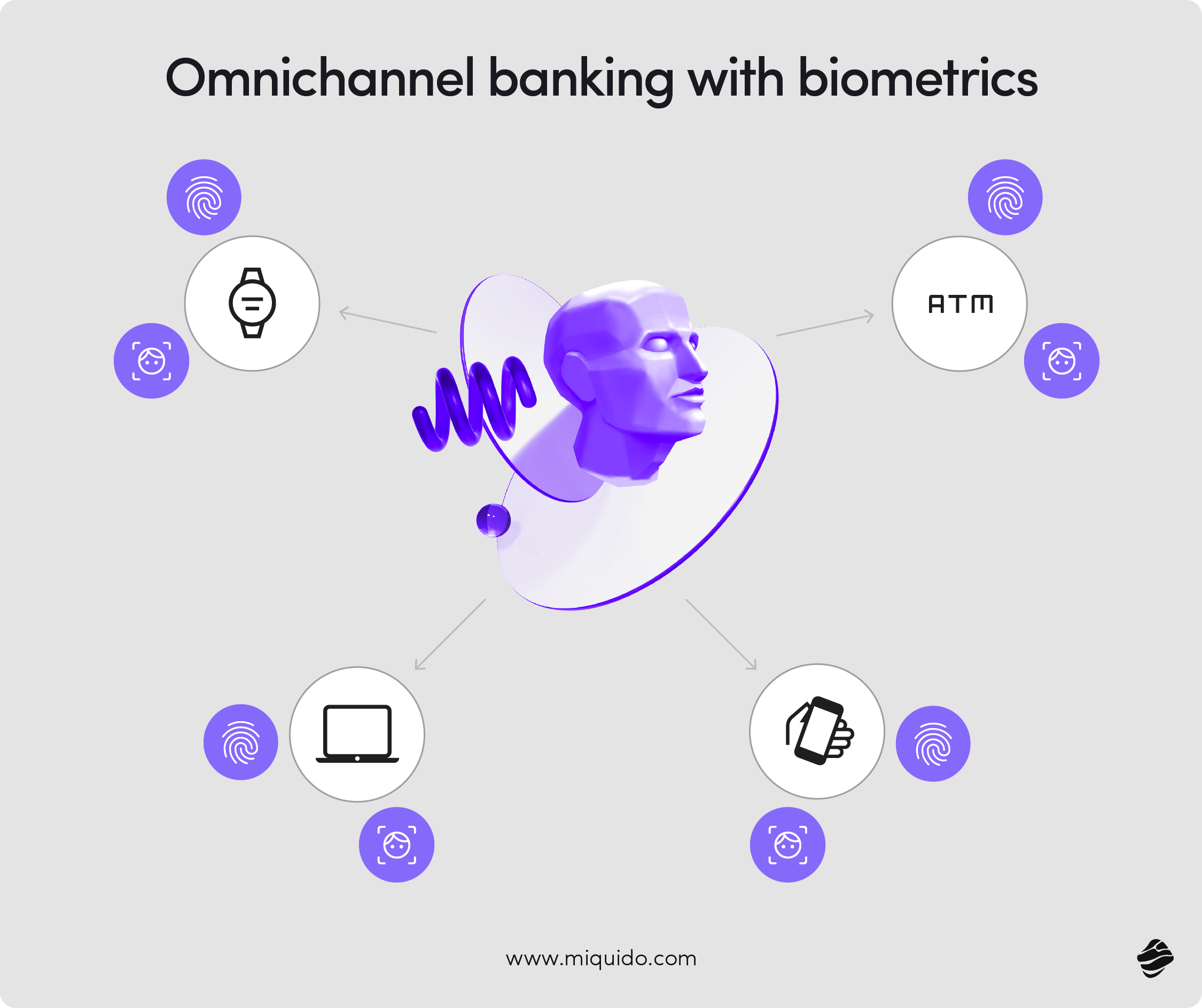
A quick story: Meet Ania, a busy small‑business owner. She opens her banking app, glances at her camera, and approves a supplier payment. No codes, no card readers, no waiting. For her, biometrics play the role of making security invisible. For the bank, the exact moment triggers background risk checks that block unusual transactions before money transfers go out the door.
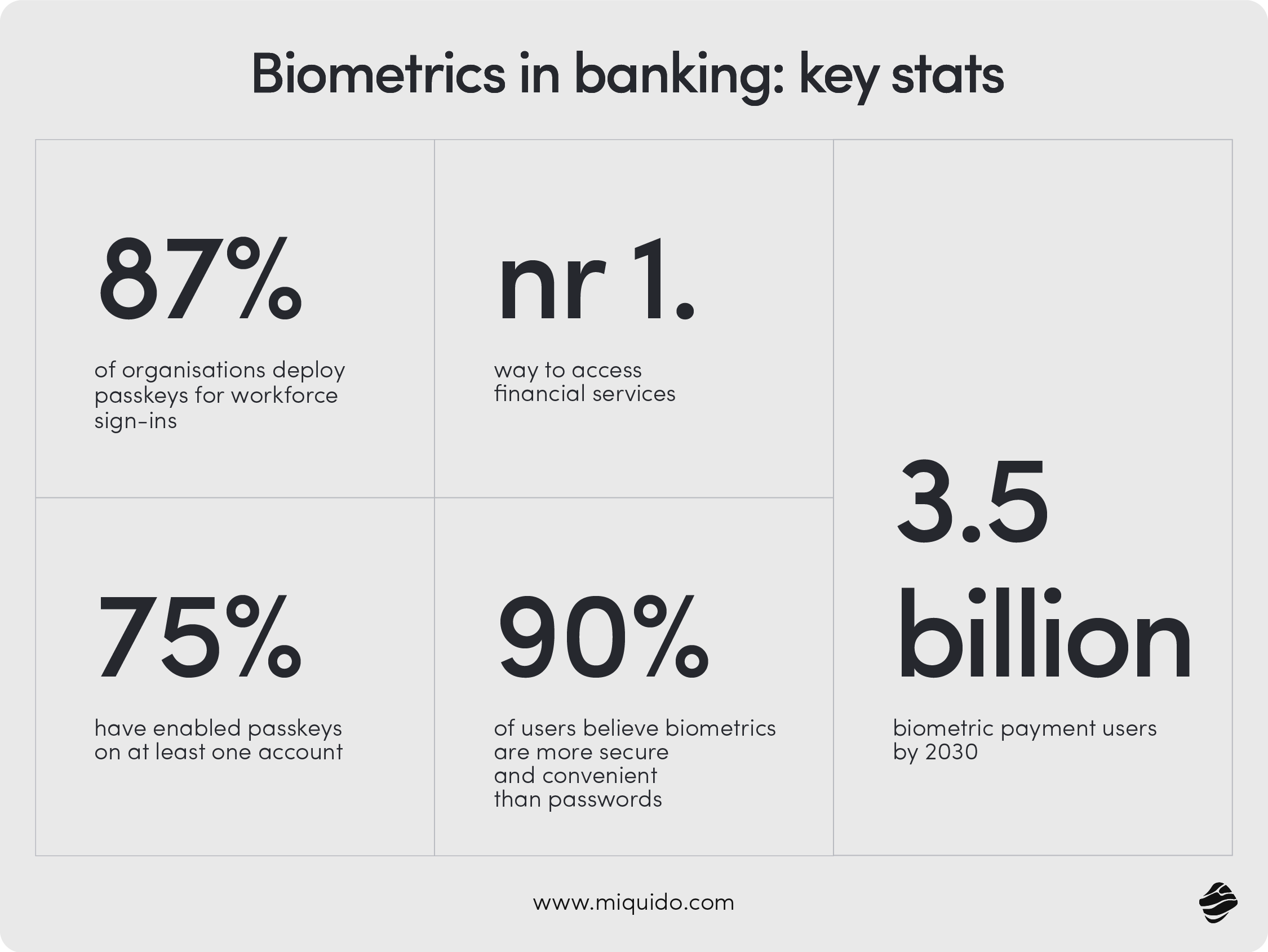
Biometrics in banking: key stats
To illustrate biometrics' impact on the FinTech industry, we gathered a few research findings.
- Passkeys/biometrics roll-out (enterprise): 87% of surveyed orgs in the US/UK have deployed or are deploying passkeys for workforce sign-ins (The State of Passkey Deployment in the Enterprise by FIDO Alliance, 2024).
- Consumers already using biometrics with banks: In a 10-country study (n=10,010), biometrics were the most common way to access financial services in the prior 60 days (e.g., 34% globally, 42% US) (FIDO Alliance Consumer Barometer 2024).
- Biometric payments trajectory (macro): Analysts forecast ~3.5 billion biometric payment users by 2030 and supplier revenue of more than $11 billion by the decade’s end (Biometric Update+, 2025).
- Passkeys sentiment (2025): Among consumers aware of passkeys, 53% believe passkeys are more secure than passwords and 54% say they’re more convenient (n=6,373). 75% have enabled passkeys on at least one account (Consumer Password & Passkey Trends, 2025).
- Mastercard perspective: Mastercard’s biometrics whitepaper summarizes research that “more than 90%” of users believe biometrics are more secure and convenient than passwords (From Password to Person: The Evolution of Biometrics, 2020).
- Behavioral biometrics in finance threat landscape: ENISA’s finance sector threat report highlights rising identity-focused attacks and the role of advanced verification (incl. behavioral biometrics) in detection (ENISA threat landscape: Finance sector, 2025).
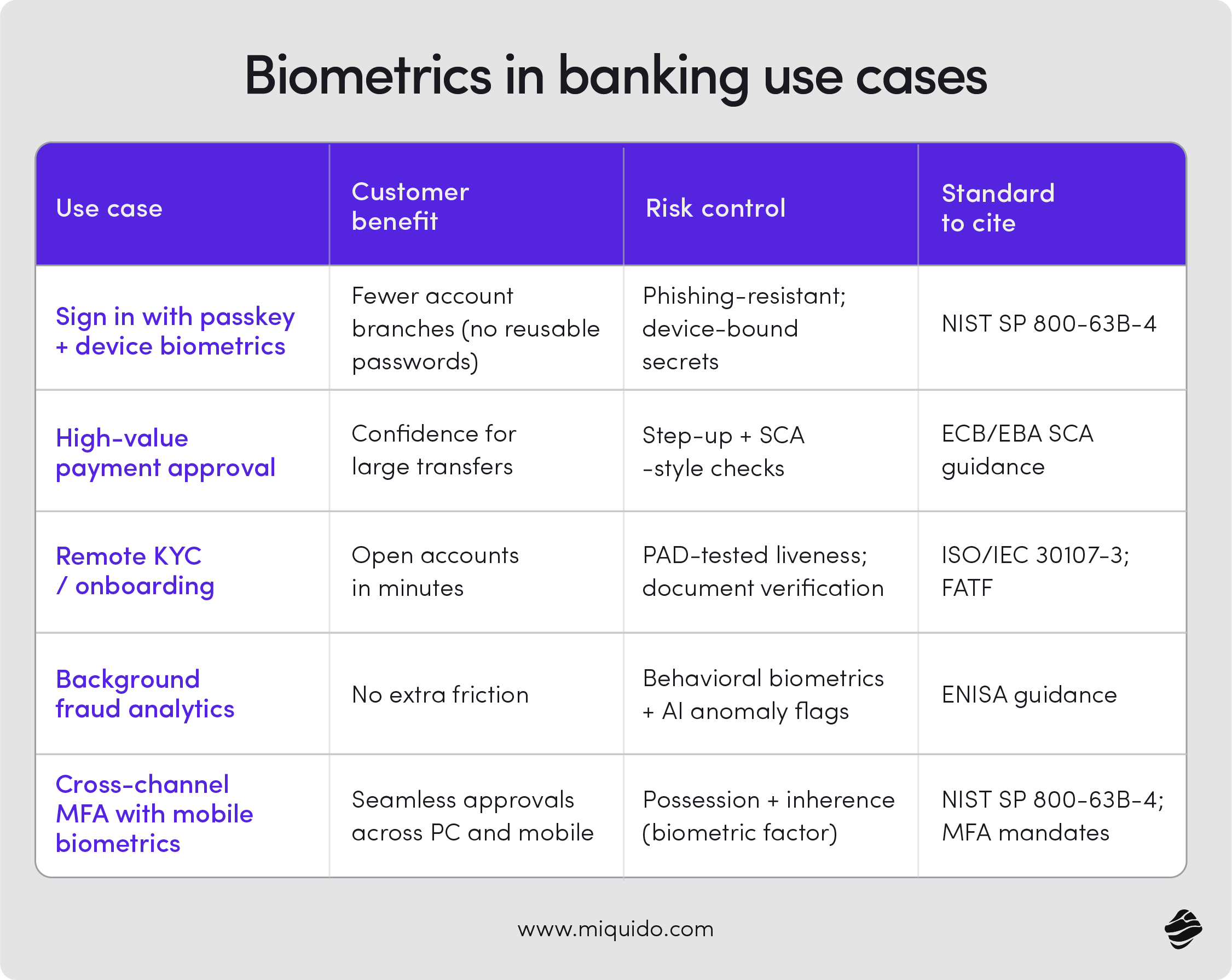
Practical use cases
Biometrics support the full customer lifecycle—from account opening to high‑risk approvals—balancing security measures with a smooth experience. Each use case blends visible steps with invisible controls that use behavioral biometrics and artificial intelligence to spot risk. For background reading, see FATF Digital Identity Guidance and ENISA Finance Threat Landscape 2025.
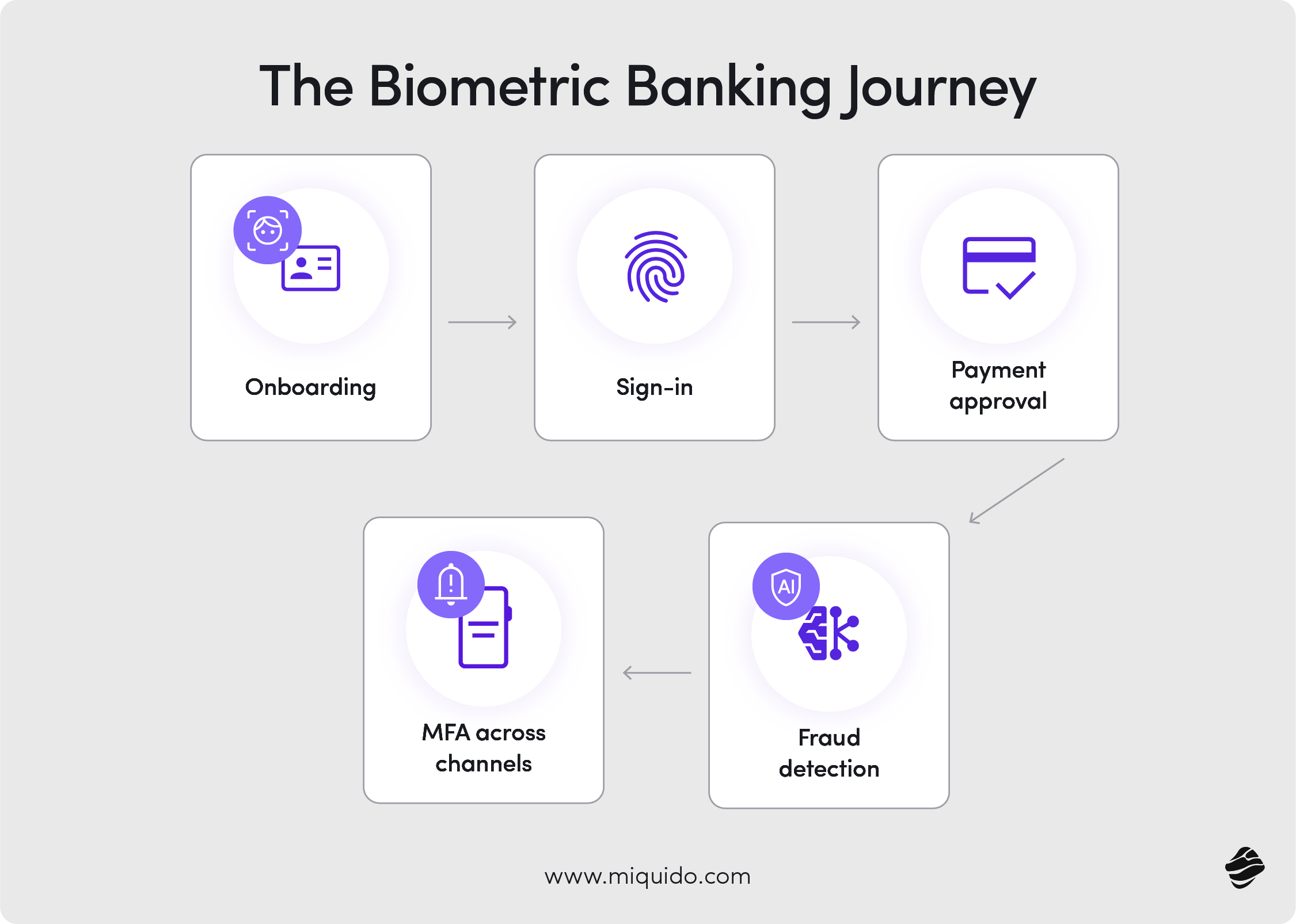
1) Account opening & KYC (Know Your Customer)
A strong first impression matters because the account opening process sets the tone for trust. When identity verification is simple and fast, more customers complete signup; when it’s clunky, they abandon the process or visit a bank branch.
How it works: Document capture plus facial recognition, liveness detection, and anti‑spoof checks verify that the applicant is real and present. These biometric verification methods compare unique physical characteristics to a reference template and confirm the user's identity for security purposes. Global AML (Anti‑Money Laundering) bodies endorse risk‑based identity verification; tailor controls to product and channel risk (FATF Digital Identity Guidance). For higher‑risk products, add video interview or in‑branch validation; for low‑risk digital banking accounts, complete onboarding fully remote.
Business benefits: Faster time‑to‑revenue, fewer manual reviews, and fewer fraud write‑offs. Clear copy explains why you ask for a face capture and how biometric data is securely stored on the device.
2) Account access & sign‑in
Login should be effortless for legitimate users and tough for attackers.
How it works: Use device biometrics—facial recognition, fingerprint sensors, or iris recognition—to unlock a passkey and streamline accessing online accounts. Add multifactor authentication (MFA) only when risk signals justify it. Align to NIST SP 800‑63B‑4 guidance on phishing‑resistant authenticators and AAL (Authenticator Assurance Level). For customers who prefer traditional methods, keep a fallback like a hardware token or a branch visit, but steer mobile consumers toward passkeys because the effort required is lower and the protection is higher.
Business benefits: Higher login success, fewer credential resets, and lower call-centre load. Because there’s no shared secret, attackers can’t reuse compromised passwords to gain unauthorized access.
3) Approving payments & other high‑risk actions
Concentrate friction where money moves.
How it works: Require biometric step‑up for large transfers, new payees, device changes, standing order edits, and credential recovery. SCA (Strong Customer Authentication) principles from payments show that targeted friction reduces fraud; similar patterns can be applied across broader bank accounts and online banking services (see ECB/EBA report). Use behavioral biometrics in the background to detect risky payee edits or device swaps and escalate to a biometric challenge only when needed.
Business benefits: Lower losses from social engineering, clearer audit trails, and better customer confidence for big moves.
4) Fraud detection in the background
Not every control has to be visible to the customer.
How it works: Behavioral biometrics and AI flag unusual transactions and sessions—typing rhythm, device posture, swipe speed—without adding steps. Pair with liveness detection to stop presentation attacks (e.g., masks, replays, deepfakes). When anomalies cross thresholds, invoke a visible biometric verification or route to a specialist team. This layered model protects digital transactions end‑to‑end (see ENISA 2025).
Business benefits: Fewer false positives, fewer abandoned sessions, and targeted reviews where they matter most.
5) Meeting MFA requirements across channels
Stronger authentication often needs more than one factor—but it doesn’t have to mean clunky one-time codes.
How it works: A mobile device with biometrics can be the second factor for actions initiated on another channel, like a PC. For example, when a user starts a transaction on desktop banking, the bank pushes a confirmation to the mobile app, where the user approves it with a face or fingerprint. This setup satisfies multifactor authentication (MFA) requirements by combining device possession (the phone) with inherence (biometrics).
Business benefits: Compliance with MFA mandates without adding friction. Customers avoid juggling SMS codes or hardware tokens, while banks deliver phishing-resistant flows smoothly across web and mobile.
Benefits: Security, UX, and compliance
Done right, biometrics increase trust and reduce friction.
This section summarizes how biometric systems and biometric security affect financial institutions' daily operations.
Enhanced security
Stop account takeovers before they start. Pair phishing‑resistant sign‑ins and biometric step‑ups with continuous risk monitoring to block misuse, while keeping clear recovery paths. Evidence from European authorities and ENISA indicates layered controls cut fraud while maintaining usability. In practice, biometric authentication helps prevent fraud by making it harder to impersonate a person's identity, because the authenticator lives on the customer’s device and is unlocked by physical biometrics.
Better experience
Reduce mental load, increase completion. Biometrics reduce the cognitive overhead of traditional passwords and one‑time codes. Approvals take seconds, and the effort required is low, which shows higher conversion, especially on mobile banking journeys. Customers recognize facial features or a fingerprint as a convenient method and alternative to card readers and SMS codes.
Compliance made simpler
Standards turn buzzwords into testable requirements. Mapping to accepted frameworks reduces audit cycles and regulator questions. Standards create a shared language for products, risks, and vendors and make results comparable. By aligning to AAL2/AAL3 (see NIST SP 800‑63B‑4), requiring PAD (Presentation Attack Detection)‑tested liveness (see ISO/IEC 30107‑3:2023), and documenting compensating controls, you can ensure compliance and demonstrate that biometric technology is used responsibly for authentication and security purposes.
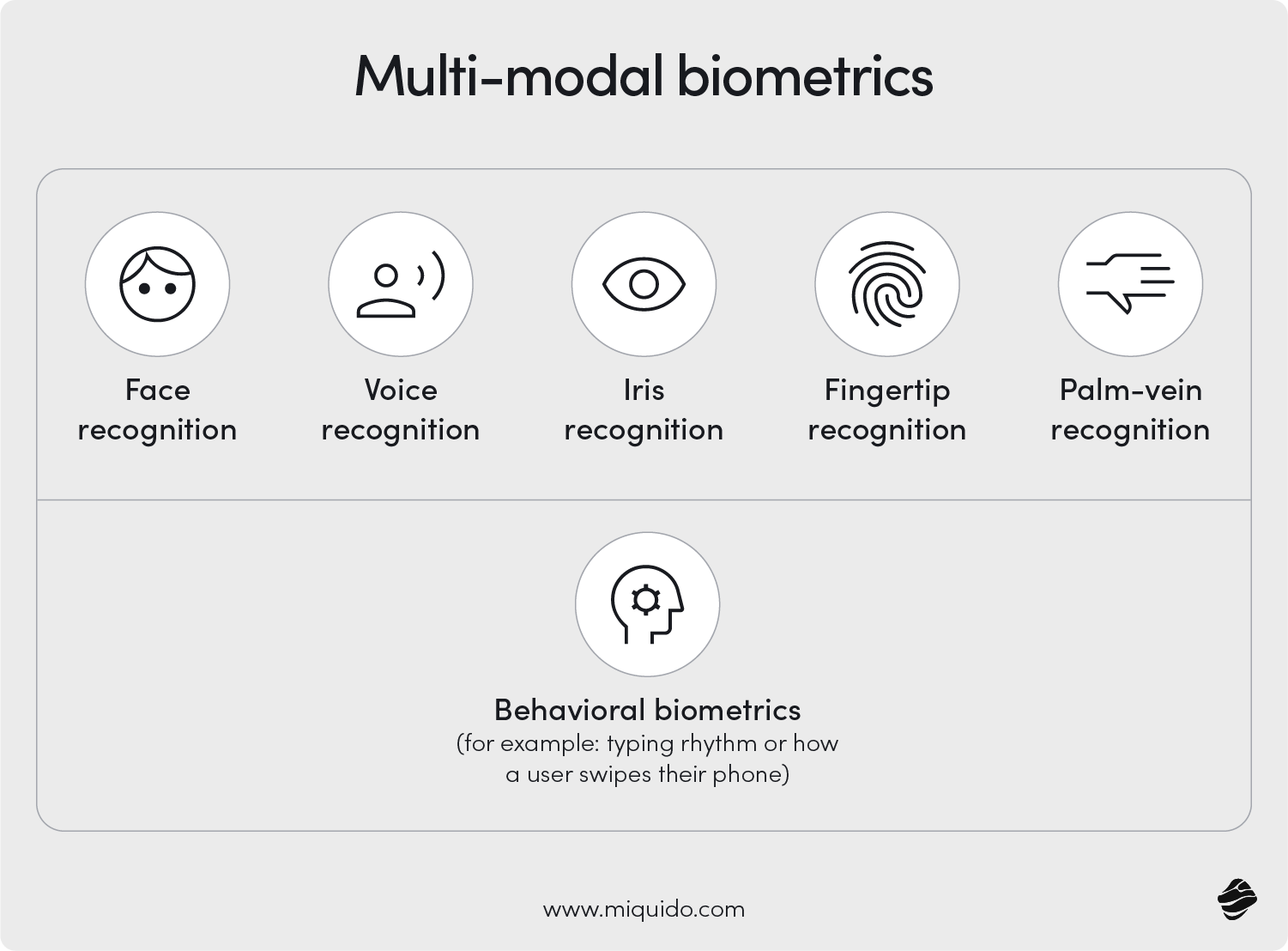
Multi-modal biometrics (why it matters): For high-assurance moments, combining two independent traits—e.g., face + liveness-aware voice, or face + device fingerprint—reduces error rates and raises spoof-resistance without forcing extra steps by default. Modern stacks fuse signals at the score/decision level, so journeys stay one-gesture for most users and only add another modality when risk is high (new device, new payee, unusual amount) or when one signal is weak (poor lighting, bandaged finger). This design also improves inclusivity (graceful fallback when a single trait isn’t available) and operational robustness (fewer false declines, clearer audit trails). Use multi-modal selectively: default single-gesture for low-risk, step up to multi-modal for money movement, recovery, and fraud-heavy cohorts.
Privacy and data handling (add to your DPIA — Data Protection Impact Assessment)
Privacy concerns should be addressed upfront with clear design choices and transparent copy. Customers are more willing to opt into biometric verification when they understand how biometric data is handled.
- Prefer on‑device biometric matching; avoid storing raw biometric data on the server side.
- Use device‑bound passkeys; minimize server exposure to shared secrets.
- Establish template lifecycle: creation, rotation, revocation, and device de‑registration.
- Vendor controls: DPAs (Data Processing Agreements)/BCRs (Binding Corporate Rules), regional data residency, and 3rd‑party test reports.
- For GDPR (General Data Protection Regulation), treat biometrics as special category data and define a lawful basis (e.g., explicit consent or other permissible bases with safeguards).
- Publish user‑facing privacy notices with plain‑language explanations of purpose, retention, and recovery options.
- Offer alternatives at a bank branch or via assisted video, so customers who prefer traditional methods still have access.
Standards and what they mean (decision aids)
Standards reduce ambiguity and help you make apples‑to‑apples comparisons during procurement. Use the three below to choose vendors, set assurance targets, and defend decisions in audits.
ISO/IEC 30107‑3 (PAD — Presentation Attack Detection)
Presentation Attack Detection is your shield against spoofing. Before you trust facial recognition to open accounts, evidence that a vendor resists masks, photos, and replays. PAD gives you a consistent way to test liveness detection (see ISO/IEC 30107‑3:2023).
Use it to: Require PAD‑conformant lab reports from candidates; reject solutions without third‑party results.
Ask vendors: Which PAD lab evaluated you? Which attack instruments (e.g., masks, replays) did you pass?
Bank impact: Fewer successful spoofs in onboarding and step‑up checks and fewer attempts to gain unauthorized access with synthetic media.
NIST FRTE (Face Recognition Technology Evaluation, 1:1)
Independent accuracy results help you pick the right engine. Different face matchers behave differently across demographics and lighting. FRTE offers a fair comparison (see NIST FRTE).
Use it to: Compare engines by false‑match/false‑non‑match rates and demographics pre‑procurement.
Ask vendors: Which FRTE track/date? What thresholds yield ≥X% TPR (True Positive Rate) at Y FMR (False Match Rate) on the latest set?
Bank impact: Better match rates at the same friction, fairer outcomes, and fewer manual escalations.
NIST SP 800‑63B‑4 (July 2025 update)
Define what “good enough” looks like for authentication. This update clarifies phishing‑resistant authenticators and AALs (Authenticator Assurance Levels).
Use it to: Map flows to AAL2/AAL3; document compensating controls; justify step‑ups for risky actions.
Ask vendors: Show how your authenticator meets phishing‑resistance and verifier‑impersonation resistance.
Bank impact: Clearer audit trail, faster approvals, and fewer policy exceptions. See NIST SP 800‑63B‑4.
Risks and how to manage them (operational)
Every control has trade‑offs. Plan for edge cases early so operations aren’t surprised later.
- Privacy: Keep matching on‑device where possible. While device biometrics stay locked in hardware, server-side handling of behavioral data and KYC documents should be minimized and tightly protected.
- Bias and fairness: Evaluate outcomes by demographic segments; manage reference image quality; provide transparent recovery paths (e.g., assisted video KYC (Know Your Customer), branch fallback).
- Fallbacks: Offer at least two non‑biometric recoveries (e.g., verified device possession + photo ID video check; or in‑branch verification). Publish expected resolution times (SLAs — Service Level Agreements). This might be especially helpful in supporting scenarios when the user loses their mobile device and is locked out.
- Threats: Use PAD‑compliant liveness detection; combine visible and invisible defenses; monitor for social‑engineering patterns and deepfakes that try to bypass biometric systems.
- Accessibility: Screen‑reader cues for prompts, low‑vision guidance for capture, localized consent text, and clear help for older devices.
- Operational playbooks: Define how agents escalate unusual transactions and what evidence is needed to restore account access.
"One often overlooked risk in biometric implementations—especially on Android—is the uneven hardware quality across devices. Some low-cost phones ship with basic “face unlock” features that simply compare two images, without the liveness detection or secure hardware backing that financial apps require. When building banking apps, relying on official biometric APIs and SDKs is essential, which exposes the device’s assurance level and lets developers restrict support to strong modalities only. This way, banks can avoid weak implementations, protect customers on less secure devices, and maintain consistent trust across their user base."
Marcin Michałek, Senior Android Developer at Miquido
What banks should do next (Checklist)
Here’s a practical rollout plan you can start this quarter. It balances speed with regulatory requirements and gives product and risk teams shared milestones.
- Choose biometric methods your users already have: facial recognition, fingerprint sensors, voice recognition, or iris recognition—validated against target devices.
- Mandate PAD and liveness: ISO/IEC 30107‑3 compliance for face/voice journeys and production‑grade liveness detection.
- Align to AAL targets: Map journeys to AAL2/AAL3; document risk rationale and compensating controls for authentication and security purposes.
- Fit every channel: Mobile devices, wearables, web, and desktop PCs—use consistent copy and support. Make sure mobile banking and online banking experiences feel the same.
- Instrument the funnel: Track login success, fraud rates, abandonment, NPS, recovery usage; run quarterly reviews and share the results with stakeholders.
- Plan change management: Train agents and banking customers on new flows, including recovery at bank branch locations.
- Vendor due diligence: Demand PAD reports and FRTE evidence; verify data residency, DPIA artefacts, and regional regulatory compliance.
- Document privacy choices: Explain why biometric data stays on the device and how templates are protected.
- Pilot with clear success metrics: e.g., +X pp login success, −Y% resets, −Z% social‑engineering losses (choose realistic targets).
- Engage Miquido: Actually, that should be our number one recommendation, as our experts will help you with every step—starting with discovery, UX, integration, testing, implementation, and compliance support.
Quick comparison table
Simple comparisons help stakeholders align on where to start and what standards to cite. Use this table in product reviews and roadmaps.
Diagnostyka case study — award‑winning mobile app
A healthcare story that mirrors banking risk and UX. Sensitive medical results demand the same protections as bank accounts and online banking data. That’s why this case is a useful proxy for high‑assurance experiences.
Context and goals: Diagnostyka, a leading medical testing brand, partnered with Miquido to deliver a secure area for results inside a consumer app. Workflows mirror banking services: fast account access, secure result viewing, and step‑up approvals for sensitive actions. The product earned recognition at the Mobile Trends Awards in 2024 and the Ways Conference in 2025.
What we implemented: On‑device biometric sign‑in, clear consent flows, granular session controls, and PAD‑aligned liveness detection to protect against spoofing. Identity verification uses facial recognition technology to confirm the user's identity before releasing access to sensitive information.
Outcomes for banking‑like flows: Higher login success, fewer resets, lower support tickets, and better completion on high‑risk steps. Moreover, with automated KYC, higher conversion from prospect to customer, and faster verification thanks to ML-based data verification. (Qualitative outcomes; client‑reported; no public numerics.)
Check out Diagnostyka's case study.
Miquido’s FinTech services (How we help)
From discovery to delivery, we translate standards into shipped product. If you need a partner who can balance security, speed, and UX for mobile consumers, Miquido has done this across regulated industries.
- Product strategy and discovery: Validate the problem, select biometric verification methods, and set AAL targets.
- UX/UI design: Plain‑language copy, accessible flows, and guidance that reduces drop‑offs.
- iOS, Android and web engineering: Deep integration with platform biometric APIs (Application Programming Interfaces) and passkeys for accessing online accounts.
- Core banking and payments integrations: Real‑time payment approval flows, alerts for unusual transactions, and ledger hooks.
- Regulatory compliance support: Security, privacy, and audits—evidence packs that ensure compliance.
- Data/AI for risk and personalization: Behavioral biometrics, anomaly detection, and risk scoring.
- Biometric systems implementation: PAD‑tested liveness, face pipelines, and secure template handling.
- AI agents implementation: Supercharge operations with assistants to triage alerts and guide recovery.
- Embedded finance and value‑added services: Extend online banking services and create new revenue streams.
Check out our FinTech services.
Key takeaways
If you remember three things, make them these. Passwordless biometrics make security simpler for customers and stronger for banks; standards make buying, building, and auditing easier; and the right partner reduces time‑to‑value.
- Passwordless, biometric sign‑ins are faster and safer than traditional passwords and scale well across mobile/web.
- SCA principles and PAD compliance reduce fraud while improving UX and helping prevent fraud in money transfers and approvals.
- Aligning to Digital Identity Guidelines simplifies audits and builds regulator confidence for financial institutions.
- Independent tests like NIST FRTE help choose engines for face verification.
- Miquido turns biometric technology into business outcomes: higher login success, fewer resets, and faster launches—proving that biometrics can be safe and seamless.
This article is revised and peer-reviewed by Marcin Michałek, Senior Android Developer at Miquido.

![[header] biometrics in banking (4)](https://www.miquido.com/wp-content/uploads/2025/10/header-biometrics-in-banking-4.jpg)



![[header] fintech super apps lessons from miquido’s development playbook](https://www.miquido.com/wp-content/uploads/2025/08/header-fintech-super-apps_-lessons-from-miquidos-development-playbook-432x288.jpg)


