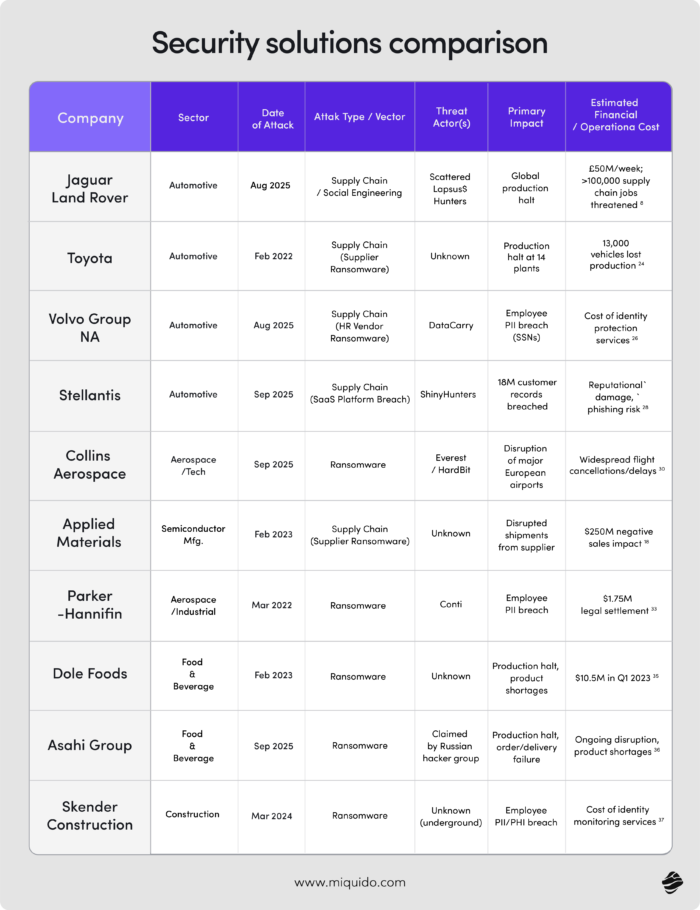
Manufacturing is not the first industry we think of as a frequent target of cyberattacks. Fintech, ecommerce and other niches where payment and customer data circulate within the digital product in large volumes – yes. But producers? However, cyberattacks against manufacturers have indeed been both rapid and dramatic in recent years. Digital integration in manufacturing has been accelerating, which has attracted
According to NTT's 2021 Global Threat Intelligence Report, the sector experienced a staggering 300% spike in attacks, causing its share of all documented cyber incidents to jump from 7% to 22% in a single year. This propelled manufacturing from the fifth to the second most attacked sector globally. This trend did not abate; by 2025, IBM X-Force data confirmed that manufacturing was the most attacked industry for the fourth consecutive year, accounting for 26% of all incidents analyzed.
It doesn’t mean you can’t defend yourself as a manufacturer – quite the contrary. The incidents of recent years can serve as a roadmap to a secure manufacturing environment. They reveal a clear pattern of vulnerabilities that threat actors consistently exploit. We analyzed the recent cases of Toyota, Volvo Group, Stellantis and more to give you a big picture of threats in manufacturing in 2025.
The following security solutions directly address these common points of failure, providing a multi-layered defense strategy for the modern manufacturing enterprise.
1. Third-party and supply chain risk management (TPRM): Key strategy for manufacturing cybersecurity
We usually hear about the cascade effect in the context of climate change. Yet a cyberattack can trigger a similar chain reaction, especially in the manufacturing industry, where supply chains form a dense web of dependencies.
When Just-in-Time (JIT) production comes into play, the consequences can be devastating, even if your company isn’t the direct target. That’s what Toyota, whose key supplier of plastic and electronic parts, Kojima Industries, was hit by a suspected ransomware attack, learned the hard way.
Because the supplier’s systems were integrated with Toyota’s JIT production model, the inability to communicate orders forced Toyota to halt operations at all 14 of its Japanese plants, resulting in a production loss of 13,000 vehicles.

This has become an increasingly common tactic among cybercriminals. Their real target is the “big fish” – in this case, Toyota – but breaching its primary security perimeter is difficult. A compromised third-party system can serve as a convenient backdoor. Given that large manufacturers often collaborate with hundreds of external suppliers, the potential attack vectors multiply exponentially.
Preventing such scenarios requires a comprehensive TPRM program – one that moves beyond simple annual questionnaires to actively assess and monitor the security posture of all external partners, from critical parts suppliers to software vendors. This means establishing mandatory security standards, conducting audits, and using continuous monitoring tools that provide visibility into the cyber risks posed by the entire supply chain ecosystem.
How a software house can strengthen TPRM
Achieving full effectiveness is nearly impossible without custom software. A manufacturer’s supplier data is often fragmented across multiple systems – Enterprise Resource Planning (ERP) for orders, Contract Lifecycle Management (CLM) for legal agreements, and separate systems for security questionnaires. Off-the-shelf TPRM tools rarely integrate seamlessly with this patchwork of business systems. On top of that, generic risk-scoring models typically fail to reflect a manufacturer’s unique operational context.
A software house can bridge these gaps by developing a centralized risk management platform with custom APIs that pull data from all relevant internal systems. This enables a unified view of each supplier, combining their security assessment data with their business criticality. The partner can then implement a bespoke risk-scoring algorithm that weighs factors unique to the your operations, making the processes semi-autonomous with manufacturing AI agents.
Such a custom solution might have flagged Kojima as a high-criticality, high-risk partner, one that required more intensive monitoring and proactive security controls.
2. Advanced endpoint detection and response (EDR/XDR): Digital vaccine for your systems
For centuries, doctors reacted to infections, treating symptoms only after the disease had spread. Modern medicine changed that. We now vaccinate, monitor, and prevent outbreaks before they begin.
In a digital sense, your endpoints – servers, laptops, operator stations, machines equipped with computer vision – are like the vulnerable points in your body, the entryways through which infections can spread. Once one is compromised, the entire organism – or in this case, the production network – can be brought down.
Yet many organizations still treat cybersecurity reactively. They rely on traditional antivirus tools that only detect known threats after they’ve already entered the system. In most industries, this lag is costly but manageable. In manufacturing, it can be catastrophic. A single infected endpoint on a production line can halt entire operations, disrupt global supply chains, and cost millions in downtime before the threat is even identified.
That’s why the security solution we recommend for manufacturing goes beyond conventional antivirus. It focuses on continuous monitoring and advanced threat detection across all endpoints, from servers to engineering laptops. EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) platforms use behavioral analysis and AI to identify anomalies, detect fileless malware, and automatically contain ransomware before it spreads. Instead of reacting to symptoms, this approach builds an immune system for your digital factory – one that learns, adapts, and neutralizes threats in real time.
3. Anti-phishing training and AI-based detection support: Taking the weight off your employees
As an end user, you’re well aware of how phishing works. You’ve probably received text messages pretending to be from your bank or a popular courier more than once. One careless click on a suspicious link, and your personal data could end up in the wrong hands.
As such attacks become more common, we’re getting better at spotting them. But things look different at work, where we can fall into a dangerous paradox. On the one hand, phishing attempts are less frequent, at least for now – they’re not part of daily work life.
On the other, they tend to be far more sophisticated. Cybercriminals understand the stakes and put more effort into their tactics. You may still stumble across simple yet effective spoofing tentative, like authentic-looking emails from rnicrosoft domain. But the truth is, phishing is getting harder and harder to detect.

Vague claims, emails that appear legitimate at first glance but are actually not directly connected to the sender, generic signatures, hidden unrelated redirect domains - these issues are often extremely hard to identify.
It’s a volatile mix that has already compromised the security of many organizations. Even giants like Facebook and Google weren’t spared – in a 2019 phishing attack, they lost a staggering $100 million.
And in manufacturing? The consequences can be just as severe. A case in point is the attack on Jaguar Land Rover (JLR) in August 2025, likely initiated through a sophisticated social engineering or vishing campaign. By manipulating employees into granting them access, the hackers managed to completely shut down JLR’s global IT systems, halting all manufacturing and costing the company an estimated £50 million per week.

So how can you protect yourself in the era of cloud-based manufacturing, when everything is interconnected? The answer seems simple: train your employees. But the reality is far more complex. 2025 UC San Diego study shows that anti-phishing training programs do not prevent employees from falling for scams. Reasons? Above all, lack of engagement and the loss of effectiveness over time. In other words, employees are not involved in the materials and they quickly forget what they have learnt.
That’s why, if you opt for training programs, they have to be thoughtfully crafted, frequent and regular. Realistic phishing simulations with interactive elements and rewards are essential. However, you might be still fighting with the windmills, and that is why we do not recommend to rely on training itself.
Generative AI, if properly trained, can support advanced phishing detection with incredible accuracy. An AI assistant, embeded in your internal tools, can support detection and train your employees at the same time by justifying its decision to the smallest detail,
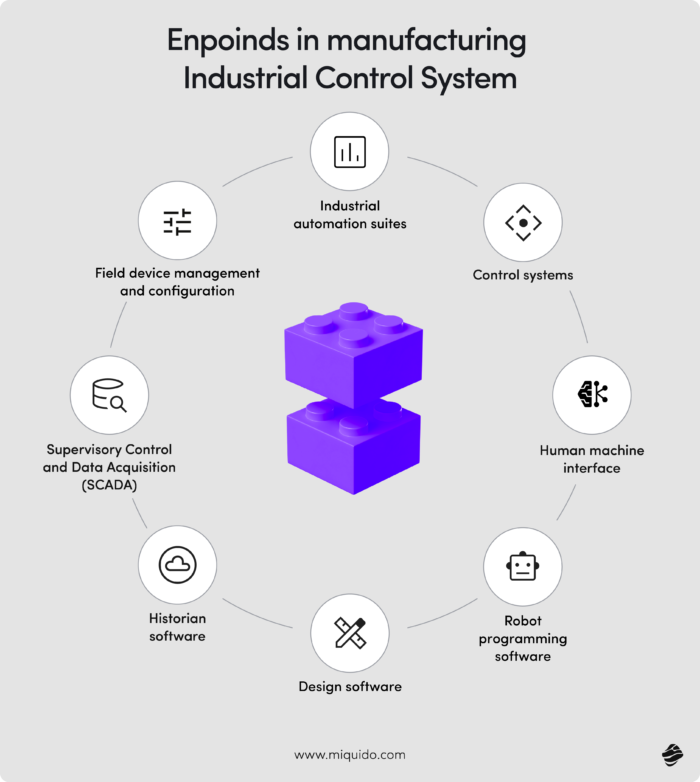
4. IT/OT network segmentation and monitoring: Digital highway patrol for manufacturers
In the early days of manufacturing automation, factory floors were islands. Machines communicated with each other over isolated, proprietary networks, and the corporate IT systems upstairs might as well have been on another planet. But in the name of efficiency and data-driven optimization, those islands have been connected – often hastily.
IoT is the essence of what is modern manufacturing today, and while it makes the factory floor much more efficient, the connected systems and devices can also turn against the manufacturers. For instance, a spreadsheet error in the office can, quite literally, stop a robot arm on the production line.
This digital convergence between IT and OT has blurred once-clear boundaries, creating an invisible highway for cyberattacks to travel from an email inbox to the factory floor. And as the Collins Aerospace attack in September 2025 showed, the consequences are no longer limited to a single organization.
When ransomware hit Collins’s MUSE passenger-processing software, an IT platform, it cascaded into the physical world. Check-in systems froze, baggage handling failed, boarding gates went dark. Airports across Europe reverted to pen and paper, flights were cancelled, and travelers were stranded. It was a textbook demonstration of what happens when IT and OT live on the same network without a proper barrier.
Effective network segmentation is like building a digital firebreak. The goal isn’t to cut communication, but to control it, allowing data to flow only through secure gateways while isolating the most critical systems. Yet implementing it is anything but simple.
Legacy OT systems often speak in decades-old dialects – proprietary protocols designed long before cybersecurity became a concern. Standard IT tools can’t “listen” to this traffic, and if they try, they might inadvertently disrupt sensitive industrial controls. Even when networks are separated, most organizations lack granular visibility into how systems talk to each other within the OT environment. And in OT, uptime isn’t just a performance metric – it’s sacred. A misconfigured scan could halt an assembly line.
Custom approach to IT/OT network segmentation and monitoring
This is where custom software becomes invaluable. A skilled software partner can develop lightweight, non-intrusive monitoring tools tailored to the quirks of your specific industrial setup.
They can build custom protocol parsers to translate obscure OT languages into something modern analytics systems can understand – safely, and without touching production. They can even create a digital twin of your factory network, a sandbox where segmentation strategies and security policies can be tested before being deployed live.
Had such tailored visibility been in place at Collins Aerospace, the ransomware outbreak might have been contained within the IT domain, sparing airports, airlines, and passengers from chaos.
5. Robust identity and access management (IAM) with phishing-resistant multi-factor authentication (MFA): Minimum permissions, maximum security
In every major breach, there’s a familiar scene: a single compromised account that opens the gates. Credentials, not code, are often the real vulnerability.
Think of your organization’s network as a secure facility. You might have walls, cameras, and guards, but if someone hands an attacker a keycard, all those defenses mean little. In the digital world, that “keycard” is your login. And as phishing grows more sophisticated, even seasoned employees can be tricked into handing it over.
What is the best defense? The principle of least privillege. Every user and application should have only the minimum permissions needed to function. And when access is required, authentication must go beyond passwords and text codes. Hardware security keys based on FIDO2 standards, for instance, are virtually immune to phishing attacks because they rely on cryptographic validation rather than user judgment.
Add password managers that work only on correct domains (UC San Diego’s recommendation) and you have a foundation for phishing-proof manufacturing environment.
Custom manufacturing security solution for better visibility
Enforcing this standards across complex manufacturing ecosystems – spanning cloud platforms, legacy systems, and partner networks – is a monumental task.
A custom software partner can help by building an integrated IAM dashboard that unifies identity data from multiple sources – Active Directory, ERP systems, SaaS platforms – into a single view. They can automate policy enforcement, detect anomalies in login behavior, and even develop a custom workflow for authorizing third-party apps.
6. SaaS security posture management (SSPM): Cybersecurity for manufacturing across the integrated apps
Cloud adoption has given manufacturers a new kind of agility, but also a new kind of blind spot. Sales forecasts in Salesforce, supplier data in Microsoft 365, production metrics in cloud-based analytics tools –– the modern manufacturing enterprise lives and breathes in Software-as-a-Service platforms. Each one is a potential goldmine for attackers, and yet most organizations have little idea what’s really connected to them.
SaaS ecosystems are porous by design. Any employee can connect a third-party app with a few clicks, often without IT’s knowledge. These “shadow integrations” can request broad permissions – access to customer data, emails, or files – under the guise of productivity tools. Multiply that across hundreds of users, and you have an invisible web of risk.
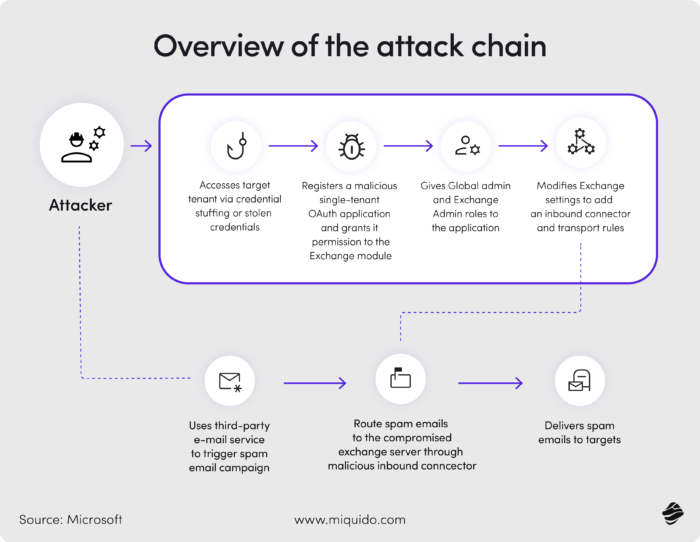
That’s exactly how the Stellantis attack unfolded: through the authorization of a malicious OAuth application. It’s not an isolated case, but rather a symptom of the SaaS explosion.
This is where SaaS security posture management (SSPM) comes in. SSPM continuously scans connected applications for misconfigurations, over-privileged access, and risky integrations, providing visibility into what’s really happening in your cloud ecosystem.
Continuity and control with custom governance automation
Even the best out-of-the-box SSPM tools struggle in manufacturing environments, where SaaS usage intersects with proprietary systems and complex access hierarchies. Revoking a permission may stop a workflow; flagging an app may disrupt production. Security teams often face an impossible trade-off between control and continuity.
A custom software partner can eliminate that tension.
Imagine a bespoke governance layer built on top of your existing SaaS platforms – a kind of internal “app store” where every integration request goes through an automated policy check. Before an app is approved, the system analyzes its requested permissions, compares them to predefined company policies, and either grants or denies access based on risk.
SSPM, backed by custom-built governance automation, ensures that the convenience of the cloud doesn’t come at the cost of security.
7. Comprehensive data backup and recovery strategy: Put out digital fires
Backups are a bit like fire extinguishers. Everyone agrees they’re important, most companies have them… and yet, when flames appear, many discover too late that they were never tested, never maintained, or weren’t designed for the fire they’re facing.
In manufacturing, downtime is existential, not just inconvienient. Every hour of halted production compounds into lost revenue, angry customers, idle supply chains, and contractual penalties. And unlike office environments, the systems involved range from databases to industrial controllers to legacy applications held together by decades of patches. Restart them in the wrong order, and the entire environment can collapse again.
That’s why simply “having backups” isn’t enough. What matters is the ability to recover – completely, quickly, and in the proper sequence.
Custom automation scripts for immediate recovery
Implementation in manufacturing is notoriously difficult. Critical systems depend on each other in ways that aren’t obvious on paper. Disaster recovery procedures often rely on engineers paging through printed checklists while a dozen teams wait for green lights. And full recovery tests are so disruptive that they rarely happen outside of emergencies – the very moment when stress and time pressure are guaranteed to produce mistakes.
This is where custom software changes the equation. A specialized partner can implement a Recovery-as-Code framework, using automation scripts to capture every nuance of your environment and orchestrate recovery from end to end.
Instead of multi-hour manual procedures, a single automated workflow can rebuild the entire production stack in the correct order. Even better, those same scripts can spin up an isolated clone of the production environment, allowing you to test your recovery plan safely and regularly, without risking real-world uptime.
8. Response (IR) planning and tabletop exercises: Better safe than sorry
Imagine a fire drill in an elementary school. The alarms sound, students line up, teachers lead the way, and in minutes everyone is outside. The drill doesn’t prevent fires, but it does prevents panic.
Cyber incidents are no different. When ransomware detonates or data starts disappearing, the clock accelerates. Every minute spent deciding who’s in charge, where logs are stored, or who can pull the plug on a compromised network is a minute the attacker is winning. Yet many organizations only begin asking those questions after the breach is already unfolding.
In manufacturing, the first hours are everything. Decisions made in that window determine whether production pauses briefly… or grinds to a halt for days.
A robust Incident Response (IR) plan assigns clear roles, defines communication channels, and outlines containment procedures long before they’re needed. It includes executive stakeholders who must decide whether to shut down lines, notify partners, or escalate to law enforcement. And critically, it eliminates improvisation.
Tabletop exercises – simulated attack scenarios – expose blind spots, miscommunications, and assumptions in a low-risk environment. They force teams to practice under realistic pressure, revealing issues that wouldn’t be obvious in calm discussion. Executives learn whom to call. Engineers learn which logs matter. Legal and PR learn how to speak publicly without revealing too much.
The organizations that survive breaches aren’t always the ones with the strongest defenses. They’re the ones who rehearsed what they would do when those defenses fail.
9. Data loss prevention (DLP) and encryption: Making stolen data worthless
Product designs, proprietary processes, customer data, supplier terms – in the wrong hands, any of these manufacturing essentials can erode competitive advantage or trigger regulatory fines.
Today’s attackers know this. They no longer simply lock up data and demand ransom; instead, they steal it, promising to leak it publicly if payment isn’t made. It’s a pressure tactic that works disturbingly well.
Data Loss Prevention (DLP) solutions operate like vigilant customs officers. They inspect data flows, classify sensitive information, and block attempts – intentional or accidental – to move it somewhere it doesn’t belong. They prevent an engineer from emailing CAD files to a personal account, or a compromised account from quietly uploading customer records to an external server.
But DLP works best when paired with a simple, powerful second line of defense: encryption. Encrypting sensitive data at rest ensures that if attackers breach a server, what they obtain is unreadable. Encrypting data in transit means even intercepted communications are worthless. To an attacker, encrypted information is scrap metal – heavy, hard to sell, and nearly impossible to weaponize.
Manufacturers often underestimate how many systems quietly store sensitive data and how many employees have access to it. DLP provides the visibility to correct that, enforcing rules based on context, not assumptions. Combined with encryption, it transforms data theft into data inconvenience.
Cybersecurity in manufacturing is more effective with custom solutions
Many of the solutions listed above work best when supported by a software team with expertise in both cybersecurity and manufacturing. Having implemented various products where security is critical, ranging from fintech to Industry 4.0, we can help you make your manufacturing ecosystem as safe as possible. Let's discuss your needs!
What are the key components of cybersecurity in manufacturing?
Cybersecurity in manufacturing involves a combination of technology solutions, human expertise, threat intelligence, and business best practices. It's tailored to protect the technology-heavy manufacturing industry from vulnerabilities in intellectual property, operational data, and supply chain information.
How prevalent are ransomware attacks in the manufacturing industry?
Ransomware attacks are alarmingly common in the manufacturing sector. Recent surveys indicate that 56% of manufacturing security solutions users experienced such attacks, with only a quarter having sufficient capabilities to mitigate damage before data encryption.
How can manufacturers improve their cybersecurity capabilities?
Essential security measures for a manufacturing plant include regular risk assessments and security audits, video surveillance systems, access control and perimeter security, physical security measures like security guards, employee training, and integrated security systems that combine both physical and cyber defenses.
How can manufacturers improve their cybersecurity capabilities?
Manufacturers can improve their cybersecurity capabilities by implementing advanced security solutions, conducting regular security audits, providing thorough employee training, and investing in integrated security systems. It's also important to stay updated on the latest threats and continuously adapt security measures accordingly.

![[header] top 9 cybersecurity solutions for the manufacturing industry (1)](https://www.miquido.com/wp-content/uploads/2025/12/header-top-9-cybersecurity-solutions-for-the-manufacturing-industry-1.jpg)


![[header] top 9 cybersecurity solutions for the manufacturing industry (1)](https://www.miquido.com/wp-content/uploads/2025/12/header-top-9-cybersecurity-solutions-for-the-manufacturing-industry-1-432x288.jpg)
![[header] b2b ecommerce for manufacturing – 21 feature ideas for cutting costs and multiplying sales](https://www.miquido.com/wp-content/uploads/2025/09/header-b2b-ecommerce-for-manufacturing-–-21-feature-ideas-for-cutting-costs-and-multiplying-sales-432x288.jpg)
![[header] top 10 generative ai use cases in manufacturing](https://www.miquido.com/wp-content/uploads/2025/07/header-top-10-generative-ai-use-cases-in-manufacturing-432x288.jpg)