In recent years, we have seen the fintech niche expand and grow rapidly. AI has accelerated the rise of new, intelligent, and personalized fintech services, while blockchain technology has paved new paths to fintech security. From online-only banks to digital wallets and exchanges, the number of available fintech apps has multiplied, and many SaaS providers in this sector have established strong audiences.
With this growth, however, comes an increasing risk. Although telecom and e-commerce companies have been hackers’ favourite targets over the past decade, fintech is becoming another key focus. As of 2024, the finance sector ranks among the top five industries with the highest exposure to threats, according to Global Threat Outlook H1-2024. It’s no wonder why—due to the high level of data vulnerability, every successful attack can be highly lucrative.

Financial security statistics
Global fintech hubs are also shifting eastward, with India’s fintech sector booming on an unprecedented scale and expected to become a $1 trillion industry by 2030. Fintech is also expanding in Africa, especially in the blockchain space. These shifts are pushing development in new directions, increasing accessibility for customers previously excluded from traditional finance and lending services.
However, digital risks continue to grow, fueled by geopolitical tensions that could disrupt industries. Conflicts such as Russia vs. Ukraine and China vs. the US could significantly ripple effects on the finance sector. The web and mobile banking app market is also becoming increasingly affected by scams and social engineering strategies. The calls from supposed banking agents who are collecting credentials by pretending to intervene in an account takeover are the rising method among scammers. That enforces changes in approach to safeguarding digital solutions, shifting attention to customer education, and expanding awareness of cyber threats.
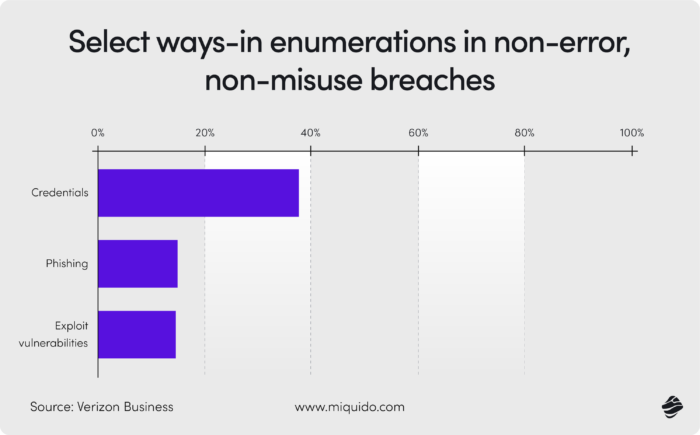
Main financial security risks
Fintech companies are challenging targets because they know the risks involved. On the other hand, the stakes are high: a successful attack can yield enormous rewards for cybercriminals. Fintech companies deal with sensitive data, so when these are encrypted, the company faces a dilemma: hefty fines for privacy violations or paying a multimillion-dollar ransom.
That all forces fintech companies face numerous threats. Areas like payment processing, account login (essential for most fintech applications), and cloud infrastructure all serve as potential attack vectors. According to the PwC 2024 Global Digital Trust Insights survey, the main vulnerability areas identified by industry participants include cloud-based pathways, attacks on connected devices, and hack-and-leak operations.
Data breaches
Data breaches are among the worst-case scenarios for companies across various sectors, particularly for fintech companies that handle highly sensitive financial data. These firms manage critical customer data—including account details, transaction histories, and personal identification—making them prime targets for hackers. For cybercriminals, these data assets are lucrative commodities, quickly sold on the black market.
Breaches can occur due to multiple vulnerabilities: weak data storage security, poor encryption standards, insufficient access controls, or even insider threats. Furthermore, the reliance on third-party integrations and cloud storage expands the attack surface, increasing the risk of breaches. The outcomes can be severe for financial institutions, leading to financial loss, reputational damage, and possible legal penalties if regulatory compliance standards are unmet.
For instance, in 2022, the fintech giant Revolut experienced a breach involving social engineering techniques, exposing sensitive data of over 50,000 customers worldwide. Although no critical information like PINs or passwords was compromised, hackers did access customer names, addresses, emails, and phone numbers, highlighting the importance of security measures. Incidents like this underscore the necessity for General Data Protection Regulation (GDPR) compliance, as well as stringent security protocols to protect customer data across fintech companies.
Ransomware
Before leaked data reaches the black market, cybercriminals often demand a ransom. Ransomware is a growing threat for fintech companies. In 2023, ransomware attacks surged by 70% compared to the previous year.
Typically, attackers gain system access through phishing or system vulnerabilities. Once inside, they move quickly to gain more permissions and reach the core of a company’s data. This is followed by encrypting the data via malware. After completing the operation, cybercriminals demand ransom, often using the data breach itself as leverage to coerce payment. However, even when companies pay, data may still leak.
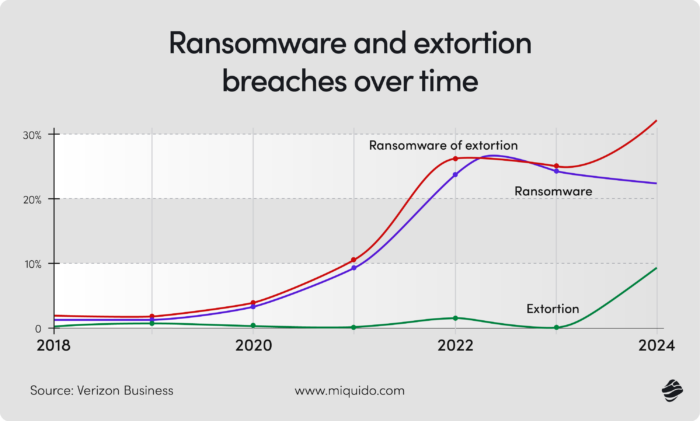
Looking at the data from Verizon’s data breach investigation report, between 2023 and 2024, the frequency of traditional ransomware attacks slightly reduced, making space for the pure extorsion method. In this method, cybercriminals proceed with threats without necessarily affecting data accessibility. In both cases, collecting evidence and collaborating with authorities without paying the ransom is recommended.
However, as reality shows, it all depends on what’s at stake. Consider a 2021 ransomware attack on Colonial Pipeline, which affected a critical fuel supply chain. The decision to pay the ransom was made instantly, considering the potential implications. The hackers provided the affected unit with a system restoration tool, but the process took over five days.
Payment frauds
Fintech apps often facilitate digital payments, transfers, and purchases, making them susceptible to fraudsters who exploit weak transaction authentication methods. Payment fraud in fintech has a direct impact on a company’s financial stability. Inadequately protected payment gateways and weak Know Your Customer (KYC) procedures often play a key role in successful frauds.
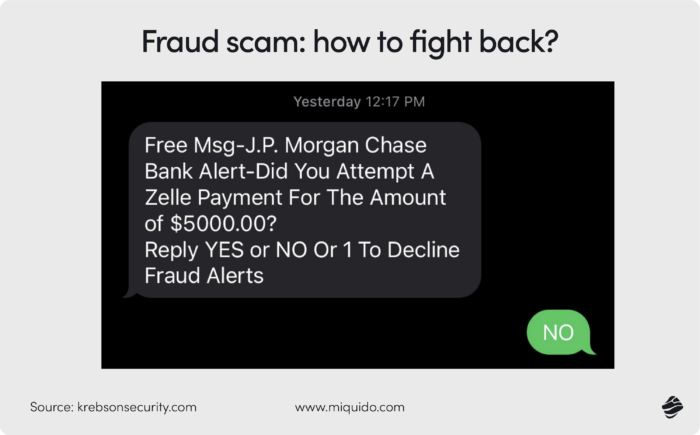
However, in the case of such fintech solutions like peer-to-peer payment systems, the main risk comes from social engineering strategies. Take the example of Zelle, a popular peer-to-peer payment app that experienced a wave of fraud affecting as much as 3% of its users at some point. Fraudsters were posing as bank fraud agents and convincing users to initiate Zelle transactions to “verify” their accounts. The irreversible nature of Zelle’s transactions left victims with no solution, with banks refusing the chargeback in most cases due to the alleged authorization process.
Insider threats
The nature of data processed by fintechs necessitates a highly hierarchical access control structure, with only a few positions having the highest access levels. Otherwise, information passing through payment gateways or APIs would be at risk. On one hand, this structure limits the pool of individuals who could intentionally cause a data leak. On the other hand, those granted such privileges could relatively freely abuse them and remain undetected for an extended period.
And it does happen. According to the Verizon DBIR 2024, insider threats account for a substantial 85% of breaches within the human element-related category. In fintech, such abuses can lead to far more devastating consequences than in other industries. Where can insider threats come from? Disgruntled employees, contractors, or third-party vendors—all of these sources pose risks for data leaks and system encryption.
How can fintech firms protect against these internal risks? Trust is important, but in this context, it should be limited to ensure peace of mind. The principle of least privilege is a fundamental defence against such abuse. This means granting access only to the data and systems necessary to perform specific job functions. To ensure the highest security, regularly review permissions and analyze user behaviour patterns to detect potential anomalies.
API vulnerabilities
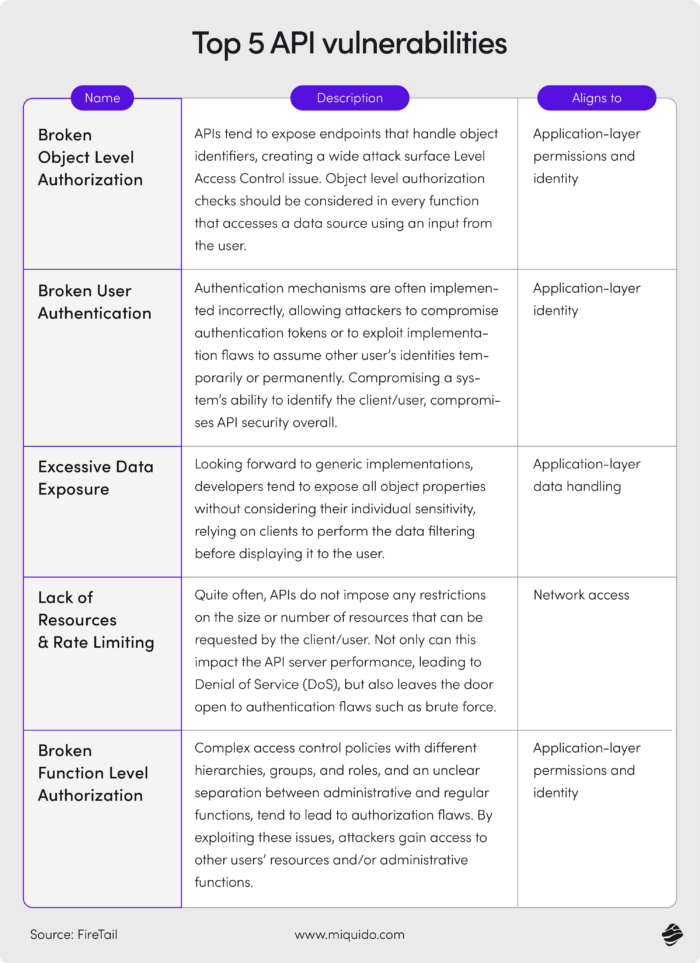
A fintech app without APIs is almost unthinkable, as APIs are essential for connections with banks, payment systems, and financial institutions. Unfortunately, APIs themselves are far from flawless. Even just weak authentication, insufficient encryption, poor endpoint security, or lack of rate limiting can allow a hacker to access an API and quickly obtain critical data.
The situation is further complicated because such attacks are difficult to detect, often relying on multiple involved parties, making effective monitoring challenging. Major companies like Twitter, T-Mobile, and Toyota have experienced firsthand the serious consequences of API vulnerabilities in recent years.
Mobile app malware
Fintech apps often run on mobile devices, making them susceptible to mobile-specific malware. Attackers target mobile fintech apps to intercept sensitive data or inject malicious transactions. Attack vectors vary and can originate from the provider’s and end users’ environments. This risk typically arises from unprotected application environments, user devices with poor security, or compromised third-party SDKs (software development kits). Users downloading apps from unofficial sources further increase the risk of malware.
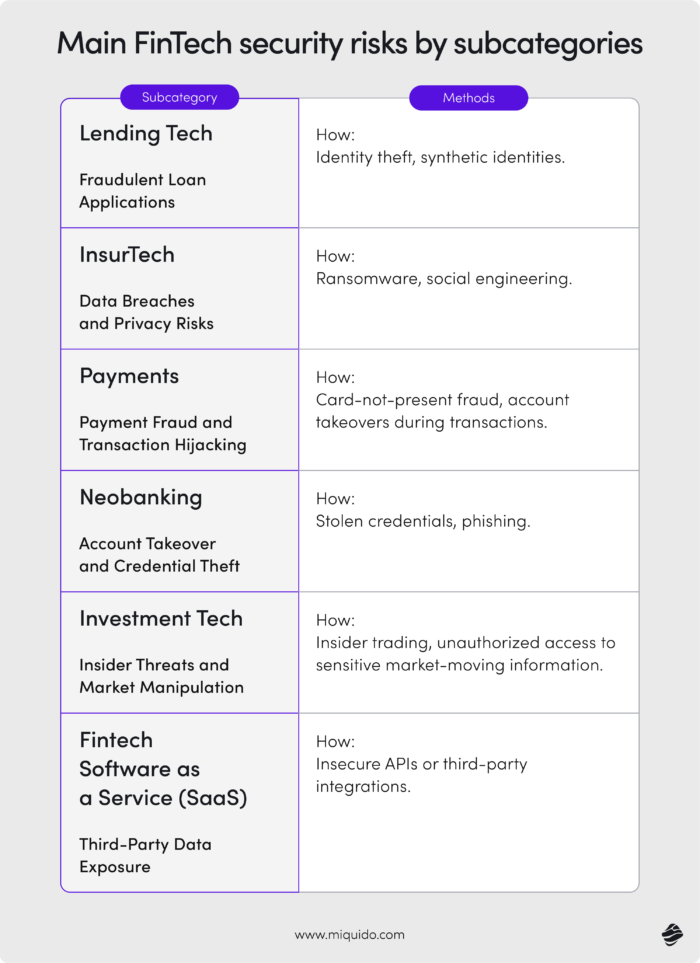
FinTech security good practices
Forewarned is forearmed, and prevention is always better than cure – especially in fintech, where every successful data breach can have heavy implications. This checklist will help you implement and cultivate safety measures that
1. Strong data encryption and secure storage
- What to do: Encrypt sensitive data both in transit and at rest. Use encryption standards like AES for data storage and TLS for data in transit.
- Why it matters: Proper encryption protects data from unauthorized access, even if systems are breached, helping to prevent data theft and ensuring user privacy.
- Tip: Due to its large key size, AES-256 is resistant to all known practical cryptographic attacks, including brute-force attacks.
2. Multi-factor authentication (MFA) and biometric security
- What to do: Implement multi-factor authentication (MFA) to add an extra layer of security, requiring users to verify their identities via SMS codes, email, or biometrics.
- Why it matters: MFA and biometric verification (e.g., fingerprint or facial recognition) significantly reduce the likelihood of account takeovers by requiring more than just a password.
- Tip: To enhance security, use context-aware or adaptive MFA, which assesses factors like location, device type, IP address, and access time. For instance, a login from an unusual location or an unfamiliar device can trigger additional verification steps.
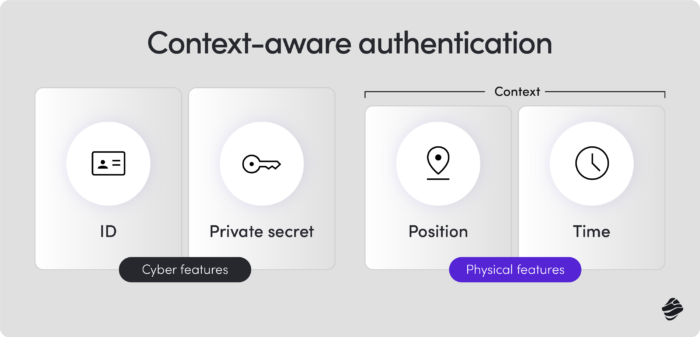
3. Continuous monitoring and threat detection
- What to do: Deploy real-time monitoring systems that identify unusual account behaviours or anomalies, flagging them for further investigation.
- Why it matters: Proactive monitoring can help detect suspicious activities early, like unauthorized access attempts or large data exfiltration, allowing for rapid responses.
- Tip: Monitor the behaviour of external accounts, but don’t forget about internal threats. Your system’s internal users should also be subject to constant monitoring.
4. Regular security audits and vulnerability assessments
- What to do: Conduct regular internal and external security audits to identify and address vulnerabilities. Perform vulnerability assessments and penetration testing to find weak points.
- Why it matters: Routine audits help discover vulnerabilities that could lead to data breaches or fraud, ensuring a resilient infrastructure.
- Tip: Some threats require perspective to be noticed – from close, they remain out of your reach. Reaching out for external company’s support is a healthy practice that can help you mantain a secure mobile banking app.
5. Secure and well-documented APIs
- What to do: Secure APIs by implementing proper authentication (OAuth, API keys) and encryption and limiting API access permissions to only necessary data. Ensure API documentation is clear and secure.
- Why it matters: Well-protected APIs prevent unauthorized access to core services and data, reducing exposure to potential breaches via third-party integrations.
- Tip: Parameter tampering can severely compromise API security. To prevent it, ensure the API only accepts specified content types (e.g., application/JSON for JSON-based APIs) and use a secure character encoding, such as UTF-8, to prevent injection vulnerabilities.
6. Robust identity verification and KYC/AML compliance
- What to do: Implement robust Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures to verify users during onboarding and monitor transactions for suspicious activity.
- Why it matters: Strong identity verification prevents fraudsters from creating fake accounts and helps fintech companies stay compliant with financial regulations, protecting both the company and its users.
- Tip: To strengthen your KYC procedures, implement automated document verification, geolocation and IP analysis. Implement stricter verification model for high-risk customers.
7. Employee training on security best practices
- What to do: Regularly train employees on security awareness, phishing prevention, and secure data handling practices. Conduct drills to test readiness and compliance with protocols.
- Why it matters: Employees are often the first line of defense, and training helps prevent insider threats, social engineering attacks, and accidental breaches.
- Tip: Implementing GenAI to scan messages and calls can help you enhance phishing prevention. The techniques are becoming increasingly sophisticated, and even employees conscious of risks may fall victim to these scams. With its NLP capabilities, GenAI can detect suspicious activity much more effectively than standard scanning tools.
8. Insider Threat Detection and Access Control
- What to do: Implement strict access controls and least-privilege access policies. Monitor insider activities and set alerts for unusual access patterns or data downloads.
- Why it matters: Limiting data access to only those who need it reduces the risk of insider threats and ensures that critical information remains secure.
- Tip: Apply SIEM (Security Information and Event Management) and UEBA (User and Entity Behavior Analytics) systems to analyze user behaviour patterns.
9. Automatic fraud detection systems
- What to d: Use AI-driven tools and machine learning algorithms to detect and block fraudulent activities, including unusual transaction patterns, in real time.
- Why it matters: Automatic fraud detection prevents unauthorized payments, reduces payment fraud risk, and provides a layer of trust and reliability in the transaction process.
- Tip: Device fingerprinting will help you enhance the efficiency of your monitoring. Collect unique device identifiers, track behavioural biometrics like typic speed, touch screen patterns and mouse movements, and monitor IP address consistency to detect the cybercriminals better.
10. Tokenization for payment security
- What to do: Replace sensitive payment data with unique identifiers or “tokens” that are meaningless if intercepted. Store original data securely on the server, away from the app environment.
- Why it matters: Tokenization reduces the risk of exposure during transactions, enhancing payment security and protecting user data.
11. Secure mobile application development practices
- What to Do: Follow secure coding practices, including the use of code obfuscation, secure SDKs, and mobile app hardening tools. Regularly update apps to address vulnerabilities.
- Why It Matters: Since FinTech apps are frequently targeted by malware, secure development helps protect the app from attacks, ensuring a safe user experience.
12. Strict compliance with industry regulations and standards
- What to Do: Stay compliant with regulations such as GDPR, PCI-DSS, SOC 2, and AML to meet legal obligations and ensure secure data handling. Regularly review compliance updates.
- Why It Matters: Adherence to regulations not only prevents hefty fines but also assures users that best practices and legal standards protect their data.
13. Incident response and recovery planning
- What to Do: Establish a well-defined incident response plan to handle security breaches or incidents. Regularly test this plan to ensure quick and efficient recovery in the event of an attack.
- Why It Matters: Preparedness reduces downtime and data loss during a security incident, allowing a fintech company to quickly regain control, minimize damage, and reassure affected users.
14. User education on cybersecurity risks
- What to do: Educate users on cybersecurity practices, including recognizing phishing scams, setting strong passwords, and avoiding suspicious links. Provide guidance on account recovery steps.
- Why it matters: Educated users are better equipped to protect their accounts, reducing the likelihood of phishing and other account takeover attempts.
DORA Directive impact
In the light of the new EU regulations, the security measures listed above gain new status, shifting from good practices to obligations. Web and mobile banking apps, SaaS fintech providers, insurance and payment systems – all are required to adjust to DORA (Digital Operational Resilience Act) until January 2025.
The directive introduces new requirements aimed at enhancing cybersecurity in fintech by boosting the operational resilience of financial entities against cyber threats, technological failures, and other potential security risks. Here are the key areas where DORA impacts fintech, along with examples of the necessary actions.
1. IT risk management
To protect sensitive financial data, fintech companies must establish a comprehensive IT risk management system that includes effective intrusion detection systems to identify and respond to incidents swiftly. This approach involves regular vulnerability scanning and penetration testing of systems to protect sensitive financial information.
Example: A fintech company offering a mobile app must conduct regular penetration tests to ensure that the app is resistant to the latest cyber attacks. DORA requires companies to show that they have processes for prompt incident response, such as integrating security with a monitoring and alert system.
2. Incident reporting
DORA mandates timely reporting of cybersecurity incidents to relevant regulatory authorities within the financial services industry, which can help minimize financial losses and improve sector-wide response coordination.
Example: If a fintech experiences a DDoS attack (a mass attack that overloads servers), disrupting financial transactions, the company must not only take corrective action but also promptly report the incident to the relevant financial industry regulatory authority. This helps enhance the coordinated response across the industry to cyber attacks.
3. System resilience testing
Fintech companies must test their systems for resilience against various cybersecurity threats, both to safeguard financial transactions and protect sensitive financial information.
Example: A fintech offering payment services should conduct continuity tests to ensure that its systems are prepared for potential server outages or internet interruptions. By testing resilience, fintech firms can better prepare for potential security risks.
4. Threat information sharing
DORA promotes collaboration across the financial services industry by encouraging institutions to share information on emerging cyber threats. This exchange allows financial entities to be better prepared for various cyber attacks.
Example: When a fintech identifies a new type of attack on their platform, sharing this information with other financial services companies can help others strengthen their own defences, thus reducing industry-wide vulnerability.
5. Third-Party risk management
Fintech companies must assess and continuously monitor the security practices of their technology service providers, such as cloud providers, as a key part of their efforts to integrate security into third-party relationships.
Example: A fintech using an external cloud provider to store customer data must perform regular audits to ensure the provider maintains high standards of cybersecurity and resilience. DORA mandates that fintech firms account for these potential security risks at the contract stage to protect sensitive financial data and minimize financial losses from third-party breaches.
Enhancing credit scoring and security: use case
Miquido’s team revolutionized the functionality of NextBank, a white-label banking solution, by implementing an advanced credit scoring system and enhancing security measures. Leveraging data analytics and AI-driven algorithms, we introduced an efficient credit scoring mechanism that enables precise risk assessments and faster loan approvals.
Simultaneously, our team prioritized robust security frameworks to protect sensitive financial data, incorporating multi-factor authentication, end-to-end encryption, and fraud detection tools. These upgrades improved the user experience and ensured regulatory compliance and trustworthiness.
At Miquido, we provide fintech app development services, implementing the listed security measures. We can help you implement AI in fintech applications at a fraction of traditional development costs and provide bulletproof solutions to the market that align with customer expectations and new DORA requirements. Let’s discuss your idea!








![[header] [ad] building a financial mobile app – an introduction](https://www.miquido.com/wp-content/uploads/2025/02/header-ad-building-a-financial-mobile-app-–-an-introduction-432x288.jpg)