Like car models or computers, software ages. Although it may still function properly, it starts to hinder progress increasingly. When everything around us advances, standing still is equivalent to falling behind.
This is particularly true in technology, which constantly moves forward. Thus, legacy systems pose a significant barrier to a company’s growth. Legacy systems tend to be extremely inefficient, leading to frustrations among users due to slow performance, long load times, and a lack of updates.
What are legacy systems? When should you consider replacing them? And how can legacy software modernization services boost business growth, based on real-life cases?
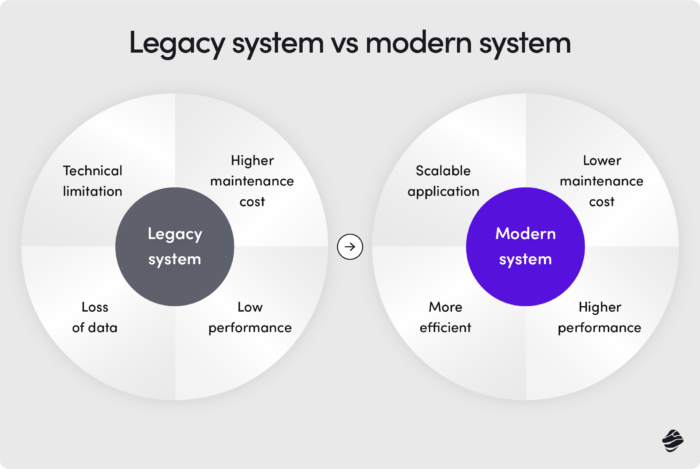
What are they? When should you consider replacing them? And how can legacy software modernization services boost business growth, based on real-life cases?
What is a legacy system?
A legacy system is an outdated software or hardware system that is still in use, despite often no longer being efficient or compatible with newer technologies. These systems are typically kept because they are critical to business operations, though they may be challenging and costly to maintain or upgrade. Maintaining legacy systems can be costly and challenging, often requiring a significant portion of an organization's budget.
A legacy system is like an old mobile phone model. It may still work well, allowing you to make calls, send texts, and take photos, but it’s incompatible with new apps and technologies, such as mobile payments or high-speed internet. Over time, these limitations only grow, making day-to-day functioning increasingly difficult.
Legacy system examples: Enterprise software
To understand what a legacy system looks like in a business setting, consider these common examples:
| Legacy system example | What it looks like | Implications |
| A 15-year-old, on-premise ERP system running inventory and payroll. | Its data is locked in a database structure that cannot communicate with your new e-commerce platform or provide real-time stock levels. | Inefficiency: Every daily stock update requires a manual data export/import, causing order delays and inventory errors. |
| Machine operating interfaces (HMI) | A human-machine interface screen on the production floor that controls a critical machine, still running on Windows XP or an unsupported Linux distribution. | Security risk: This unpatched system is a prime target for ransomware, leading to an immediate and total production shutdown. |
| The monolithic backend | A single, massive codebase (a "monolith") built years ago that handles all orders, payments, and customer management from one centralized application. | Innovation blockade: Adding a simple new payment option requires months of development and risks crashing the entire website upon deployment. |
A very common example of legacy processes in companies is the paper-based document circulation. While it technically works, searching through documents is time-consuming, and accessing specific data is difficult compared to modern, digital databases. On top of that, customers are getting used to handling matters digitally, further complicating operations.
Adding the increasing tendency among governments to enforce digitalized invoice circulation and integrating it becomes obvious that sooner or later this legacy process will become not only a burden but also a significant barrier.
What can turn your system into a legacy system?
The term "legacy" is often used interchangeably with "old." However, this is a mistake. Not every old system is a legacy system. What typically qualifies a system as a legacy is the widespread adoption of new technologies that are crucial for a company’s operations. In recent years, we have seen several such shifts, moving even well-functioning systems into the "legacy" category.
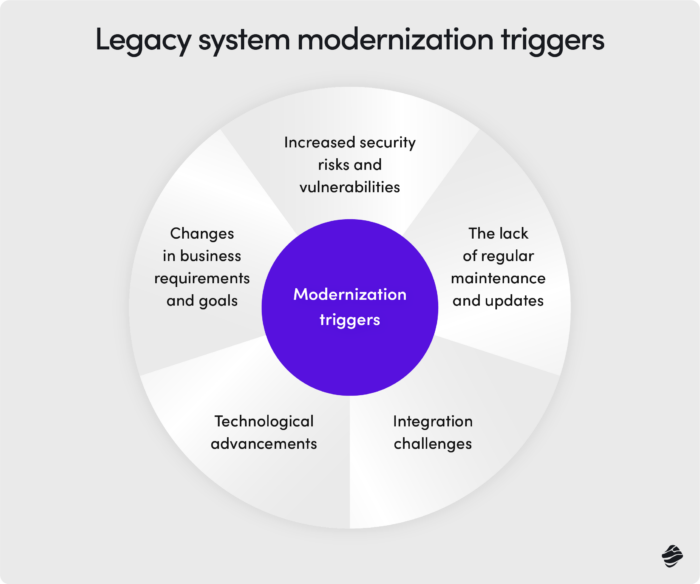
A system can become a legacy system for several reasons, each contributing to its gradual obsolescence. Key factors include:
- The lack of regular maintenance and updates. Just like a car that needs periodic servicing to run smoothly, software systems require consistent updates to stay functional and secure. When these updates are neglected, the system becomes outdated software, struggling to keep up with modern demands.
- Changes in business requirements and goals can also render a system obsolete. As companies evolve, their operational needs shift, and systems that once fit perfectly may no longer align with new objectives. This misalignment can lead to inefficiencies and hinder growth.
- Technological advancements play a significant role in turning systems into legacy systems. As new technologies emerge, older systems may struggle to integrate or compete, making them less effective. For instance, the rise of cloud computing and mobile solutions has left many on-premise systems behind.
- Integration challenges further highlight a system’s limitations. When a legacy system cannot seamlessly connect with newer systems, it creates data silos and operational bottlenecks. This lack of compatibility can stifle innovation and slow down business processes.
- External regulatory pressures and law changes often force obsolescence. New governmental regulations (like GDPR, HIPAA, or SOX) impose mandatory requirements for data handling, security, and auditing. Systems not originally designed with these complex, legally mandated features often become non-compliant and legally risky, requiring massive and expensive re-engineering or replacement.
- Lastly, increased security risks and vulnerabilities make legacy systems a liability. Outdated security protocols and unsupported components can expose the system to cyber threats, emphasizing the need for modernization to protect sensitive data and maintain trust.
However, it is not always a matter of technological progress. Turning points in history that bring about far-reaching changes in work organization can also turn many solutions into legacy systems.
To understand potential triggers better, here are examples of legacy systems that widely impacted us globally both on business and individual level.
Legacy processes modernized: Public health data pipeline rehaul triggered by Covid-19
Legacy processes can keep on going for decades: they are inconvenient, sometimes cause minor bottlenecks, but everyone looks at it as "part of the inventory." They work... until they don't. When something unexpected, unprecedented happens, they can become impossible to rely on, from day to night.
That's precisely what happened with the COVID-19 pandemic, which suddenly challenged the data processing pipelines of State and Local Public Health Departments in the US. Believe it or not: before 2021, the patient data was mainly faxed and manually re-entered into governmental registers. Delays and errors were commonplace. In the pandemic, this suddenly became painfully felt; with such an influx of patients, this system could not function.
The Department of Health and Human Services (HHS) stepped in to solve this critical data bottleneck not by replacing the entire healthcare system, but by rapidly building a secure, centralized, and digital platform called HHS Protect.
Launched in April 2020, HHS Protect became the "common operating picture" for the whole-of-government response. It served as the central hub to collect, integrate, and share COVID-19 data in near-real time across federal agencies and with state, local, territorial, and tribal partners. It brought together data from more than 300 sources.
By centralizing and digitizing the data flow, HHS Protect transformed scattered information into nationwide situational awareness, which was essential for allocating scarce resources and guiding public policy. The shared, timely hospitalization data allowed federal agencies to make informed decisions on resource allocation, such as distributing testing supplies, medical personnel, and therapeutics.
The sword of regulation: How GDPR turned systems into instant liabilities
The decision to replace legacy software is often postponed because the systems, while ancient, still function. But when the regulatory bodies decide to enforce changes and raise the cost of non-compliance to an existential level, "working but old" systems may soon turn legally dangerous liabilities.
The key example? The GDPR (2018). It imposed consumer rights, most critically the right to erasure (the right to be forgotten), putting companies functioning in the EU across all sectors in trouble.
Older systems, designed to indefinitely hoard data across fragmented databases (data silos), had no automated function to permanently track down and delete all traces of an individual upon request. This architectural flaw created a massive legal risk, as non-compliance could lead to fines of up to 4% of global annual turnover. The system's inability to comply with this fundamental privacy mandate instantly turned the software into a toxic asset, requiring an immediate and fundamental architectural re-engineering.
In both the SOX and GDPR cases, the legislation did not mandate a specific technology; it mandated a level of risk mitigation. By raising the penalty for non-compliance to such a high degree, these external regulatory triggers forced business leaders to abandon functional but non-compliant legacy systems, proving that legal liability is often the single most powerful driver for radical software modernization.
Types and examples of legacy IT systems
Depending on what trigger turned your system into a legacy system, you can categorize it accordingly. Custom-built software is at risk, but even off-the-shelf software can become outdated systems. This often happens in cases such as:
- Mainframes (computers with high computing powers, but difficult to adapt to modern digital demands),
- Custom-built software without vendor support,
- On-premise solutions that are incompatible with cloud services,
- Solutions with rigid architecture preventing integration via API and adjustment to various operating systems,
- Solutions based on outdated languages or frameworks that hinder development.
Every software project has a unique "fingerprint" in its code - the specific way it implements business logic. A new team's ability to be effective hinges on understanding this implementation. Without that knowledge, they will be slow to deliver value and far more likely to introduce new bugs.
Piotr Mitkowski, Flutter Tech Lead at Miquido
Challenges of legacy systems: what can legacy technology lead your company to?
If you were to ask any entrepreneur whether outdated solutions positively impact innovation, the answer would be obvious. NTT's research clearly shows that 80% of organizations agree that inadequate or outdated technology is holding back innovation. However, in practice, entrepreneurs often ignore the early warning signs and wait until the last minute, when problems have piled up.
Many companies fall into a trap: why replace something that still works? Indeed, the issues caused by legacy systems are usually only mildly noticeable at first. The beginnings are often innocent—an inability to integrate with a key data source, reduced efficiency, or lack of access to online files. Over time, however, these issues begin to significantly affect the company and expose it to increasing losses.
What is the biggest challenge in the context of legacy systems?
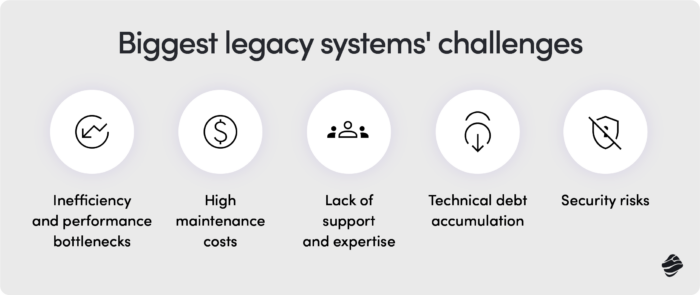
Security risks
Legacy software can contain vulnerabilities that pose significant cybersecurity risks. Outdated security protocols may serve as an open door for cybercriminals. Legacy software often relies on outdated user access practices and outdated dependencies, such as unsupported libraries or unpatched components, which can create vulnerabilities and increase the risk of cyberattacks.
For instance, in manufacturing, machine operating interfaces (HMIs) often run on severely outdated Windows XP or unsupported systems. These machines are sometimes isolated, giving a false sense of security. However, any connection (e.g., a maintenance laptop) can be an 'open door' for a hacker to compromise the entire Industrial Control System (ICS), leading to a complete production shutdown. The initial problem is minor—just an old screen—but the consequence is catastrophic short-term downtime and long-term reputational damage.
That can lead to severe consequences. For instance, consider the SolarWinds attack in 2020, which severely impacted the entire supply chain. SolarWinds became the target of a massive cyberattack due to outdated and poorly secured software.
High maintenance costs
Legacy systems prevent changes, which in itself involves costs. On top of that, there are maintenance costs that arise for several reasons. First, legacy systems often rely on outdated hardware and software components that are expensive to repair or replace. Many parts and technologies used in these systems are no longer in production, driving up the cost of maintaining them.
The maintenance cost isn't just server electricity. It’s the hidden tax of having to hire an expensive, niche contractor every time a minor bug fix is needed, or spending thousands of dollars to purchase a single, specific replacement hardware component because the original manufacturer went out of business a decade ago. This cost accumulates over the long term, turning apparent savings into crippling expenses.
Inefficiency and performance bottlenecks
When scaling becomes a challenge, business growth is hindered. Legacy systems can negatively impact productivity, preventing teams from implementing improvements and responding to new business challenges as they arise. Integrating legacy systems with modern tools is challenging, stopping the team from automating their work and elevating efficiency.
Lack of support and expertise
Owners of legacy systems must face the lack of qualified specialists, as many experts move on to other niches with advancing technology. This makes it difficult to find not only a development team but also support in emergency situations when the system fails. This can easily lead to costly, time-consuming downtimes that damage both finances and reputation.
Technical debt accumulation
By using legacy systems, companies gradually accumulate technical debt. When they finally decide to replace the system, finding competitive specialists may prove difficult, and the cost of changes significantly higher than just a few years ago. To bridge the growing technological gap, companies may opt for quick, not necessarily well-thought-out changes to achieve their goal and complete digital transformation. This creates an ideal environment for accumulating technical debt.
Legacy software and its impact on business growth
Recent technological advancements pose significant challenges to the growth of companies still relying on legacy systems. Modern innovations such as cloud computing, artificial intelligence, and machine learning have become essential tools for improving efficiency, scaling operations, and driving personalized customer experiences. However, legacy systems, with their rigid structures and limited integration capabilities, struggle to accommodate these new technologies.
As businesses increasingly leverage big data for strategic decision-making and personalization becomes the norm, companies operating on legacy systems find themselves at a disadvantage. Competitors seamlessly integrate AI-powered tools and real-time data analytics, whereas legacy systems hinder such initiatives, making data flow between different systems inefficient and slow. This technological lag not only limits a company’s ability to innovate but also diminishes its agility in responding to market changes, ultimately impeding growth and eroding its competitive edge.
Assessing and planning for legacy system modernization
Legacy system modernization is a complex process that requires careful assessment and planning. To ensure a successful transition, organizations must take a structured approach, starting with a thorough evaluation of their existing systems. Legacy system modernization strategies strongly depend on the state of the art, and every modernization of legacy systems should be preceded by an in-depth analysis.
Identifying legacy systems
The first step in the modernization journey is identifying which systems qualify as legacy systems. This involves conducting a comprehensive inventory of all existing systems and applications. Evaluate each system based on its age, functionality, and compatibility with modern technologies. Assessing system performance, security, and reliability will provide insights into which systems are most in need of an upgrade.
Determining the business criticality of each system is also crucial. Some legacy systems may be deeply integrated into daily operations, making their modernization a high priority. By understanding the scope and impact of your legacy systems, you can prioritize efforts and allocate resources effectively.
Evaluating business needs and goals
Once you have identified your legacy systems, the next step is to evaluate your business needs and goals. Start by assessing your current business processes and requirements. Identify areas for improvement and opportunities for innovation.
Defining clear modernization objectives and key performance indicators (KPIs) will help guide your efforts. Align these objectives with your overall business strategy to ensure that modernization efforts support your long-term goals. This alignment will maximize the benefits of legacy system modernization, driving efficiency, and growth.
By following these steps, you can prepare for a successful legacy system modernization, ensuring that your systems remain relevant and effective in an ever-evolving technological landscape.
Benefits of legacy modernization
Legacy system modernization can bring numerous benefits, both for the company itself and its teams. It increases the company's competitiveness in the market, enhances its resilience to market changes, and, despite the necessary expenses, translates into significant long-term savings. Moreover, modernizing an existing system helps businesses stay agile in their digital transformation journey, ensuring they can handle modern security threats more effectively.
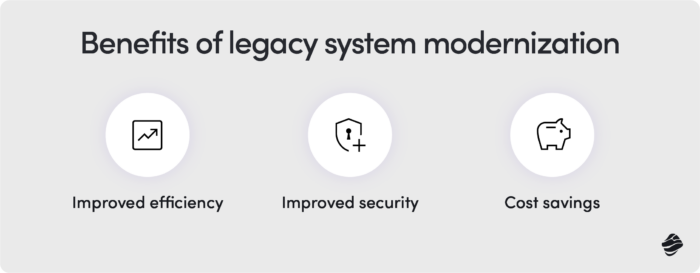
Improved efficiency
In an optimized system, the team has the opportunity to work more efficiently. Manual and unnecessary processes are eliminated through automation, with no barriers to implementation. Unlike older ones, newer systems can integrate smoothly with external tools, allowing employees to streamline their work. As a result, IT systems become more reliable, reducing the risk of system failures that can hinder productivity.
Improved security
The benefits related to increased security often go unnoticed—until an actual threat occurs. Older systems, with their outdated protocols, may leave room for significant security vulnerabilities. It's better not to tempt fate. With legacy system modernization, you can eliminate vulnerabilities in libraries and outdated security and access protocols, allowing you to handle modern security threats and prevent system failures that could result from breaches. This is especially critical for mainframe systems that have been in operation for decades.
Cost savings
As mentioned, the longer you delay updating your current legacy system in the face of significant technological shifts, the higher the cost the market will impose on you. Modernizing saves money in multiple ways: on hard-to-find specialists needed to maintain legacy technologies, on reducing IT system downtimes due to a lack of experts, and on preventing lost business opportunities.
Additionally, upgrading ensures better compatibility with modern technology, avoiding the need for expensive custom fixes. You also make better use of your existing data, as modern systems can handle it more efficiently, unlocking further potential for cost savings. In the long run, it's a win-win scenario!
How to modernize legacy systems? Modernization techniques and approaches
Choosing the right strategy for modernizing legacy software depends on the technological shift or trigger that the company needs to adapt to. In some cases, a small change might be enough, while in others, it will be necessary to rebuild the entire system from scratch. Much also depends on the architecture and language of the current system.
- Is the problem related to the readability of the code itself?
- Is there a shrinking number of specialists on the market experienced in working with such systems?
- Or does the system block development, limiting your ability to leverage new functionalities and emerging technologies that are becoming the standard in your industry?
There are many scenarios and several possible paths to address them. Let’s look at these—from the lightest to the most comprehensive.
Lift-and-Shift
This strategy is strictly data-focused and is often chosen by companies that, for example, want to enable effective remote work, freely use SaaS tools, and leverage the full potential of data across various areas of their operations.
In the past, companies have resorted to this strategy in the face of significant obstacles in executing their current business model. A great example is Netflix, which moved to the cloud in 2008 due to major shipping disruptions—a move that proved highly successful.
The lift-and-shift strategy does not require redesigning the application, which means it can quickly generate significant savings. However, it may require certain compromises that wouldn't be necessary with more radical strategies.
When it is suitable:
- Enabling remote work: When a company needs to quickly make its systems available online to accommodate remote workforces without changing the underlying application logic.
- Using cloud infrastructure: When cost reductions or improved scalability are needed by moving from on-premises servers to cloud hosting, but the system is functioning well otherwise.
- Avoiding downtime: When the company requires a quick migration to a new platform (e.g., cloud migration) with minimal downtime, particularly during urgent business disruptions.
Refactoring old systems
In the case of refactoring, companies rewrite portions of the legacy system to improve functionality and integrate better with new technologies. This strategy is a step up from lift-and-shift because it requires intervention in the code. Importantly, it is more about reorganizing the code than fully replacing it. This type of intervention does not change the code's external behavior but simply addresses maintainability issues. The code becomes more readable and easier to work with, especially for new or less experienced team members.
For many companies, refactoring is a routine practice and an integral part of Agile software development. However, some companies opt for it only when further software development starts to present serious difficulties and takes longer than expected. It’s helpful to think of refactoring like weeding a garden—one weed here and there might not hurt, but as weeds spread, your software will lack the space to flourish.
When it is suitable:
- Improving code quality: When developers find it increasingly challenging to add new features or fix bugs due to poorly structured code.
- Onboarding new developers: When new team members struggle to understand and maintain the code due to its complexity or lack of readability. It can also lead to IT staff augmentation challenges.
- Reducing technical debt: When the accumulated shortcuts and workarounds in the codebase significantly affect productivity and software quality.
Refactoring should be prioritized over a full rewrite. While the process may seem more complex, it allows the delivery of the new value to continue. A rewrite risks trading known problems for new, unforeseen ones. With refactoring, we retain control by addressing issues we already understand.
Piotr Mitkowski, Flutter Tech Lead at Miquido
Replatforming legacy systems
Another method, similar in nature to lift-and-shift, is replatforming. In this scenario, significant changes to the software architecture are not made. However, replatforming requires more intervention in the legacy system.
The main goal of replatforming is to adapt the software to work in a different environment, often to achieve better efficiency or scalability. This involves some optimizations or updates to make the software more suitable for the new platform, without fundamentally changing the code’s architecture. Unlike lift-and-shift, replatforming often includes upgrading databases, changing hosting providers, or tweaking middleware. This way, the software can better utilize the features of the new environment.
When it is suitable:
- Adopting cloud-native features: When the company wants to migrate to the cloud and take advantage of cloud-native services like managed databases, auto-scaling, or containerization without rewriting the entire application.
- Optimizing system performance: When performance improvements can be achieved through minor modifications to work better with the cloud environment, such as changing the type of database or using more efficient cloud services.
- Reducing platform dependencies: When the company wants to move away from outdated hardware or hosting platforms that no longer support business growth, while still preserving the core functionality of the application.
Replacing legacy systems
Sometimes, the most beneficial move is to go all-in with a complete system replacement. This approach may take more time, but it can solve all of your problems simultaneously while leaving the door open for further changes and innovation. Whereas the earlier methods typically address a specific issue, complete replacement is a multi-solution. It doesn’t always have to involve building a custom solution from scratch, although that path often proves to be the most worthwhile.
If you’re going to tackle obstacles, it’s better to do so thoroughly rather than swapping one problem for another—something that unfortunately often happens with off-the-shelf solutions, as they are designed for a broader group of users, even if they do have a specific niche.
When it is suitable:
- Aging system beyond repair: When the existing system is outdated and no longer supports business growth, making further updates or patches ineffective or too costly.
- Customization needs: When the company has very specific, unique requirements that off-the-shelf software cannot accommodate, and a tailored solution is needed to align perfectly with business objectives.
- Technological leap: When the organization wants to take advantage of the latest technologies, such as AI or advanced analytics, which are impossible to integrate effectively with the current system.
Overcoming legacy system challenges: real-world examples and solutions
Companies are not always eager to boast about transitioning to a new system that frees them from legacy. After all, it requires admitting that something wasn’t functioning quite as it should and may have exposed user data to potential risks. On the other hand, practices like upgrading legacy systems through refactoring are routine and don’t require public disclosure. However, more radical changes are sometimes announced publicly.
The legacy software modernization cases we've gathered show that such a drastic shift is both possible and worthwhile. Some are still in progress, while others have already demonstrated the positive effects of such upgrades. Let’s take a closer look at them and see if they share any common factors.
Megaport and Lufthansa systems partnership
Let's start with a fresh collab aiming to tackle modern logistics challenges. Lufthansa Systems, which provides IT services to over 350 airlines, partnered with Megaport to modernize its IT infrastructure with advanced digital transformation services. This involved leveraging Megaport's Software Defined Network (SDN) for transitioning to a multi-cloud environment, enabling Lufthansa Systems to securely and reliably connect cloud-hosted applications. We'll still have to wait for the effects of this updgrade, but without a doubt, they will be impressive!
AWS mainframe modernization and Banco Inter
Banco Inter, a leading digital bank in Brazil, utilized AWS Mainframe Modernization to migrate their mainframe applications to a cloud environment, resulting in substantial cost savings. The modernization also significantly improved customer experience, as the bank now processes hundreds of thousands of transactions daily and maintains 99.99% uptime for critical services.
Banco Inter delivers approximately 150 application updates weekly, a process that previously took up to two hours but now takes only five minutes. Additionally, this scalability has enabled Banco Inter to process over 100,000 transactions per minute, making it the first fully cloud-operated bank in Latin America, and one of the largest Microsoft infrastructures running on AWS in the region.
Streamlining Dolby On: How Miquido took over and enhanced app development
Miquido took over the development of the Dolby On app after the previous vendor became unavailable, focusing on enhancing both Android and iOS versions. Despite the initial challenge of a quick handover, Miquido refactored the code, streamlined features, and improved user experience by adding functionalities like batch delete and export options.
The team's successful collaboration across multiple time zones led to significant increases in app downloads, activations, and user retention, starting a long-term partnership with Dolby for additional projects.
Nubank's legacy system modernization using Flutter
Nubank modernized its legacy systems by adopting Flutter, allowing them to create cross-platform mobile apps with a unified codebase. This switch improved development speed, reduced costs, and enhanced app stability.

The modernization led to faster product updates and a consistent user experience across iOS and Android, significantly boosting customer satisfaction and operational efficiency. For more details, see Nubank's showcase on Flutter.
Foodnotify: Project takeover for UX and performance boost
Foodnotify built a platform to manage the supply chain and inventory for the hospitality sector, focusing on reducing food waste. While the core idea was strong, the initial development resulted in accumulated technical debt, poor code quality, and slow feature delivery.
Miquido took over the project, starting with a technical audit to identify core issues. After, we designed an iterative refactoring roadmap and updated the platform's tech stack (Symfony, PHP, Flutter). On top of that, we implemented an offline-first approach for core inventory tasks, ensuring uninterrupted business operations regardless of network stability.
PKO Bank Polski's migration to the cloud
In 2023, PKO Bank Polski, one of the leading Polish banks, successfully modernized its legacy IT systems by migrating to a more scalable cloud-based infrastructure. This transformation helped PKO Bank leverage advanced analytics and offer new, more flexible digital services to its customers. The move to modern technologies also enabled better data management and integration with new banking platforms, which contributed significantly to improving customer service and operational efficiency.
Poczta Polska and its digital revolution
The national postal service, Poczta Polska, is planning to undertake a major modernization of its IT systems, transitioning from outdated software to a new platform that supports logistics, customer service, and financial operations. This shift will enable the company to improve package tracking, streamline internal processes, and enhance overall service delivery in response to the growing demand for e-commerce deliveries. The main aim? Removing bureaucracy, that has been stopping Poczta Polska from growth and getting rid of long-term technological debt generated by over 20-years old systems.
Legacy technologies and the skill gap: the COBOL dilemma in banking
A notable example of legacy systems fitting the last category is COBOL in banking. COBOL is considered legacy technology because it is an outdated programming language developed in the 1960s and still running many legacy systems in the financial infrastructure today. These outdated systems pose significant security risks and block growth due to inflexible frameworks and data silos. Legacy system integration with modern technologies such as AI or blockchain is literally impossible, and that is a serious roadblock on a path to innovation.
Many experts with COBOL knowledge are retiring, creating a shortage of professionals for existing legacy system maintenance. This skill gap, along with the rising demand for adaptable new systems to counter modern security threats, makes financial institutions reliant on COBOL vulnerable to disruptions. These disruptions can lead to failures in adapting to regulatory changes or even severe operational and security risks, necessitating replacing legacy systems with more agile solutions.
The COVID-19 pandemic became a major catalyst for organizations to replace their legacy systems, exposing the limitations of outdated software like COBOL. US unemployment systems, many of which were over 40 years old and still reliant on COBOL, struggled to process the surge in claims, affecting millions of people. The shortage of COBOL programmers further compounded the issue, making it difficult to maintain or update these systems in real-time. This situation underscored the urgency for modernization, as outdated software was not only inefficient but also unable to adapt to the rapid changes brought on by the pandemic.
Future outlook on the legacy system challenges
As the AI revolution advances, we will likely see many companies modernize their legacy systems in the upcoming years. The shift will likely be significant, especially in banking, where many still rely on outdated backends. In industries like eCommerce, where the pressure for advanced data usage and personalization is the strongest, this change has already been ongoing, but the modernization trend will only strengthen.
The main trigger for rapid legacy updates might be the rise of cyberattacks. Between 2021 and 2023, data breaches rose by 72% according to ITRC Annual Data Breach Report. Although phishing is the main strategy on the rise, the outdated technologies and protocols often serve cybercriminals as an easy way in.
The velocity-scale paradox: When "vibe code" becomes a toxic liability
The decision to build a solution is often driven by the desire for speed and immediate results. The newest frontier in this rapid deployment is vibe-coded or no-code/low-code software, built by "citizen developers" to solve pressing business needs using accessible platforms.
The initial success is dramatic: a critical process is digitized in days, not months. But the very velocity that creates the initial win also creates the most pernicious legacy trap, transforming a functional tool into an unmaintainable liability the moment the business scales.
The trap is sprung when the business’s need for customization, performance, or deep enterprise integration exceeds the proprietary platform’s capacity, effectively forcing a complete, costly rewrite of the system.
| Legacy trap mechanism | Description |
| Vendor lock-in and data captivity | The system’s logic and data structures are wholly owned by the platform vendor. Unlike custom code, the application cannot be simply exported and migrated. When the business hits a technical ceiling or the vendor's subscription costs become prohibitive, the only option is a costly architectural rebuild to extract the trapped data and replicate the functionality on a custom stack. |
| The maintenance ceiling | The visual workflow becomes the modern version of "spaghetti code." Logic flows, built by a single individual (often outside IT governance), grow complex, convoluted, and undocumented. When the builder moves on, the opaque system instantly becomes an orphaned asset: unreadable, unmaintainable, and impossible to audit or update safely. |
| Shadow IT security risk | Built without centralized IT oversight, these systems frequently store critical data (PII, financials) without proper security protocols, audit trails, or vulnerability testing. The solution, functional in its business context, poses a massive and often unknown compliance risk, turning it into a silent, ticking liability that is one breach away from being a catastrophe. |
In this scenario, the software's functional utility remains, but its non-compliant architecture, high-cost ceiling, and total dependence on a proprietary vendor or single employee mandate a sudden, critical, and complete technological overhaul.
Prevent and solve legacy software challenges with Miquido
At Miquido, we provide legacy systems modernization services, ensuring both scalability and safety of your solution. If you want to make your systems architecture future-proof, we can make it happen, taking care of the ideation, design, development, app maintenance and support.